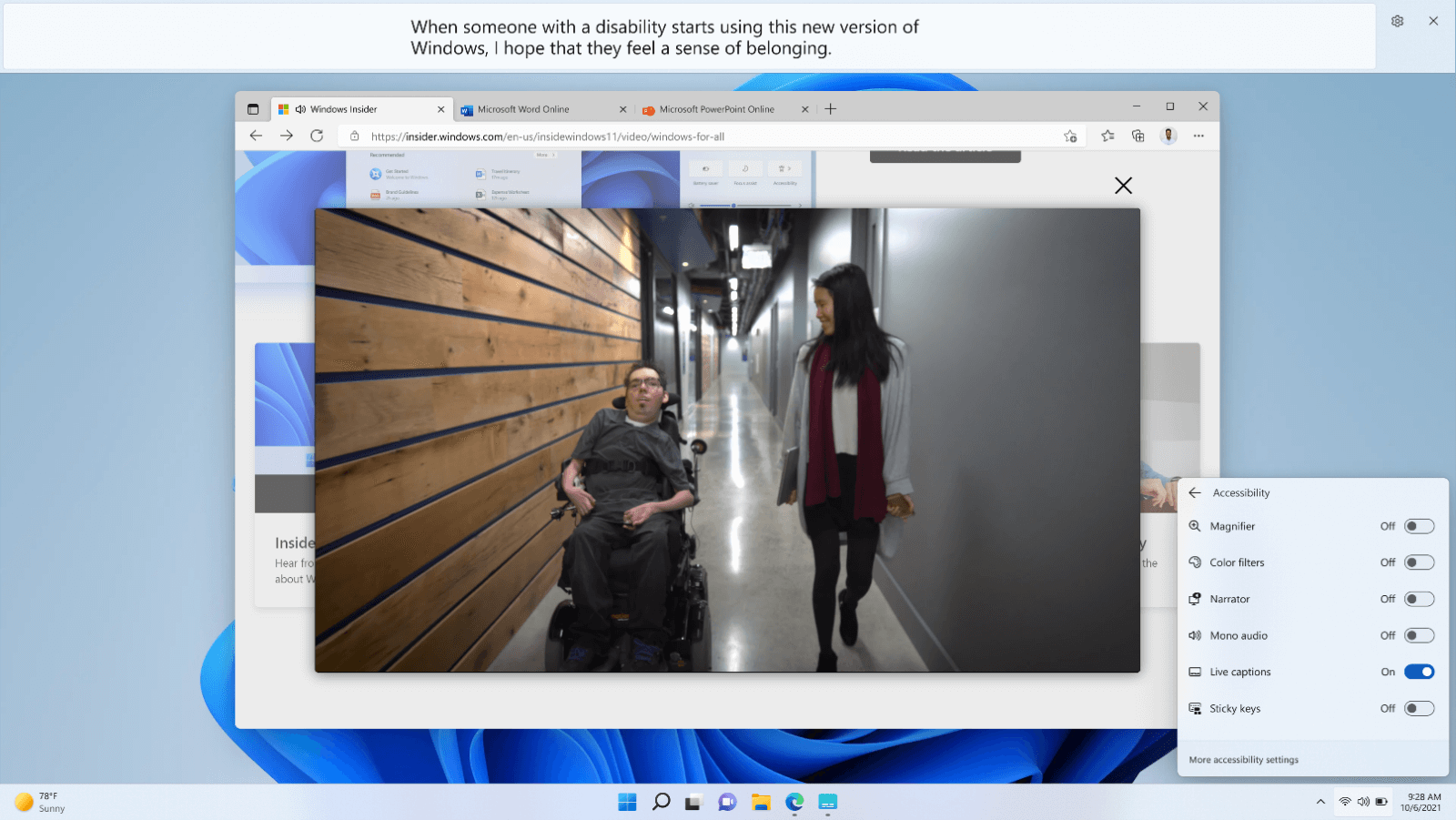
Avatars for Microsoft Teams – lets your users connect with presence in Teams without having to turn on their cameras
Avatars for Microsoft Teams – lets your users connect with presence in Teams without having to turn on their cameras
Archive for Mai, 2023
Microsoft 365 – turn on your avatar while in a Teams meeting
Mittwoch, Mai 31st, 2023FRITZ!Smart Gatway – erweitert ihr euer FRITZ! Smart Home um Zigbee Kompatibilität
Mittwoch, Mai 31st, 2023Freunde des Stroms – Kaskadenschaltung Wärmepumpe Photovoltaik PV Überschuss Wärmepumpe und Haus mit Heizstrom nutzen
Mittwoch, Mai 31st, 2023Pi-hole – you can easily block e.g. zip domain by adding a blacklist regex
Mittwoch, Mai 31st, 2023\.zip$
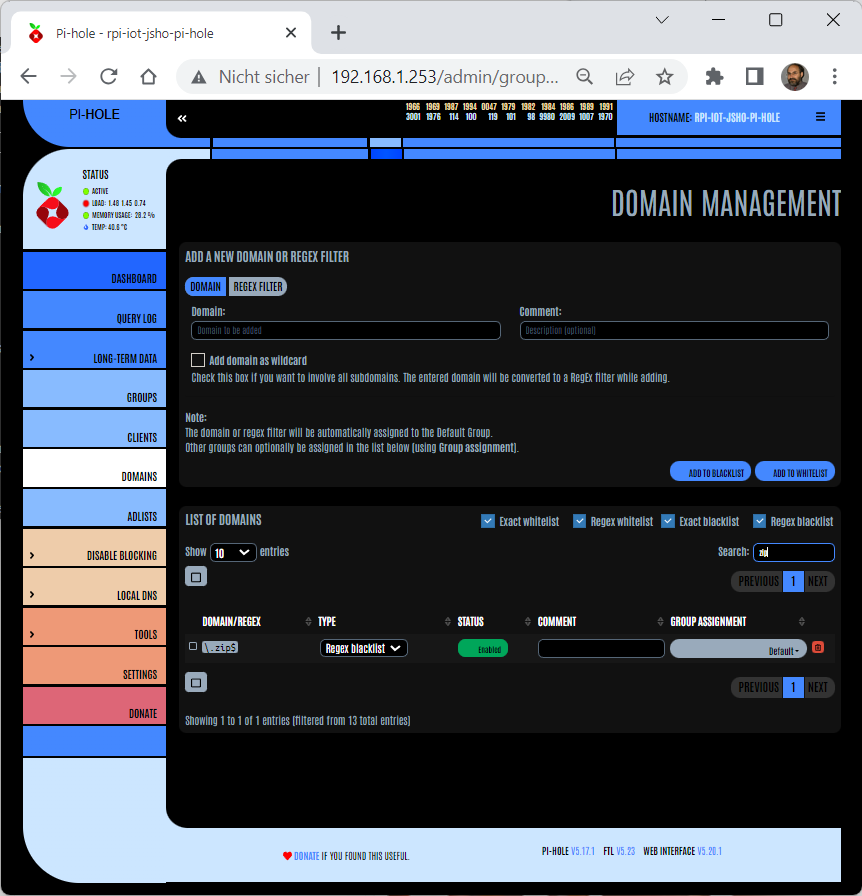
.ZIP Domain – so kann auch ein Hacker Angriff gestartet werden
Mittwoch, Mai 31st, 2023OCS Inventory NG 2.10.0 – how to build an IT asset inventory server
Mittwoch, Mai 31st, 2023Prof. Dr. Edmund Weitz – was sind Äquivalenzrelationen
Mittwoch, Mai 31st, 2023Google Chrome Version 114.0.5735.110 – steht zum Download bereit
Mittwoch, Mai 31st, 2023Linux command ‚lscpu‘ – Informationen zur Prozessorarchitektur anzeigen
Mittwoch, Mai 31st, 2023root@PVE-MINIO-01:~# lscpu
Architecture: x86_64
CPU op-mode(s): 32-bit, 64-bit
Byte Order: Little Endian
Address sizes: 40 bits physical, 48 bits virtual
CPU(s): 2
On-line CPU(s) list: 0,1
Thread(s) per core: 1
Core(s) per socket: 1
Socket(s): 2
NUMA node(s): 1
Vendor ID: GenuineIntel
CPU family: 15
Model: 6
Model name: Common KVM processor
Stepping: 1
CPU MHz: 3192.746
BogoMIPS: 6385.49
Hypervisor vendor: KVM
Virtualization type: full
L1d cache: 64 KiB
L1i cache: 64 KiB
L2 cache: 8 MiB
L3 cache: 32 MiB
NUMA node0 CPU(s): 0,1
Vulnerability Itlb multihit: KVM: Mitigation: VMX unsupported
Vulnerability L1tf: Mitigation; PTE Inversion
Vulnerability Mds: Vulnerable: Clear CPU buffers attempted, no mic
rocode; SMT Host state unknown
Vulnerability Meltdown: Mitigation; PTI
Vulnerability Mmio stale data: Unknown: No mitigations
Vulnerability Retbleed: Not affected
Vulnerability Spec store bypass: Vulnerable
Vulnerability Spectre v1: Mitigation; usercopy/swapgs barriers and __user
pointer sanitization
Vulnerability Spectre v2: Mitigation; Retpolines, STIBP disabled, RSB fil
ling, PBRSB-eIBRS Not affected
Vulnerability Srbds: Not affected
Vulnerability Tsx async abort: Not affected
Flags: fpu vme de pse tsc msr pae mce cx8 apic sep mtr
r pge mca cmov pat pse36 clflush mmx fxsr sse s
se2 syscall nx lm constant_tsc nopl xtopology c
puid tsc_known_freq pni cx16 x2apic hypervisor
lahf_lm cpuid_fault pti
root@PVE-MINIO-01:~#
root@PVE-03:~# lscpu
Architecture: x86_64
CPU op-mode(s): 32-bit, 64-bit
Byte Order: Little Endian
Address sizes: 36 bits physical, 48 bits virtual
CPU(s): 4
On-line CPU(s) list: 0-3
Thread(s) per core: 1
Core(s) per socket: 4
Socket(s): 1
NUMA node(s): 1
Vendor ID: GenuineIntel
CPU family: 6
Model: 58
Model name: Intel(R) Core(TM) i5-3470 CPU @ 3.20GHz
Stepping: 9
CPU MHz: 604.615
CPU max MHz: 3600.0000
CPU min MHz: 1600.0000
BogoMIPS: 6385.78
Virtualization: VT-x
L1d cache: 128 KiB
L1i cache: 128 KiB
L2 cache: 1 MiB
L3 cache: 6 MiB
NUMA node0 CPU(s): 0-3
Vulnerability Itlb multihit: KVM: Mitigation: Split huge pages
Vulnerability L1tf: Mitigation; PTE Inversion; VMX conditional cache flushes, SMT disabled
Vulnerability Mds: Vulnerable: Clear CPU buffers attempted, no microcode; SMT disabled
Vulnerability Meltdown: Mitigation; PTI
Vulnerability Mmio stale data: Unknown: No mitigations
Vulnerability Retbleed: Not affected
Vulnerability Spec store bypass: Vulnerable
Vulnerability Spectre v1: Mitigation; usercopy/swapgs barriers and __user pointer sanitization
Vulnerability Spectre v2: Mitigation; Retpolines, STIBP disabled, RSB filling, PBRSB-eIBRS Not affected
Vulnerability Srbds: Vulnerable: No microcode
Vulnerability Tsx async abort: Not affected
Flags: fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts a
cpi mmx fxsr sse sse2 ss ht tm pbe syscall nx rdtscp lm constant_tsc arch_perfmon peb
s bts rep_good nopl xtopology nonstop_tsc cpuid aperfmperf pni pclmulqdq dtes64 monit
or ds_cpl vmx smx est tm2 ssse3 cx16 xtpr pdcm pcid sse4_1 sse4_2 x2apic popcnt tsc_d
eadline_timer aes xsave avx f16c rdrand lahf_lm cpuid_fault epb pti tpr_shadow vnmi f
lexpriority ept vpid fsgsbase smep erms xsaveopt dtherm ida arat pln pts
root@PVE-03:~#
Bayerischer Digitalgipfel 2023
Mittwoch, Mai 31st, 2023Microsoft Windows 11 22H2 – use live captions to better understand audio
Dienstag, Mai 30th, 2023Italy Lago Maggiore und die Borromäische Inseln – online webcam
Dienstag, Mai 30th, 2023Großglockner Hochalpenstraße – ein zu 100% elektronisch betriebener 12m langer Niederflur- und Panoramabus
Dienstag, Mai 30th, 2023Wireshark 4.0.6 – we do not ship official 32-bit Windows packages for Wireshark 4.0 and later
Dienstag, Mai 30th, 2023 Wireshark 4.0.6 – release notes
Wireshark 4.0.6 – release notes