Archive for the ‘VMware Info’ Category
VMware Host Client Beta – bringing back the desktop app
Mittwoch, April 10th, 2024Nutanix Community Edition (CE) – Exploring Nutanix from a VMware User’s Perspective
Freitag, April 5th, 2024VMware Tools 12.4.0 | 21 MAR 2024 | Build No 23259341 – release notes
Samstag, März 23rd, 2024VMware by Broadcom – customers have reported price hikes of as much as twelve-times (1.200 %) even if they are invited to relicense VMware software
Donnerstag, März 21st, 2024
VMware vSphere Hypervisor (ESXi 8.x) Update 2b – release notes
Mittwoch, März 6th, 2024 VMware vSphere Hypervisor (ESXi 8.x) Update 2b – release notes
VMware vSphere Hypervisor (ESXi 8.x) Update 2b – release notes
VMware vSphere 8.0 Update 2b – as part of the VMware vSphere Foundation offering you can use up to 100 GB of vSAN storage per vSAN host licensed core without applying a vSAN licensing key
VMware by Broadcom – New Licensing Models
Mittwoch, März 6th, 2024VMware by Broadcom – Produkte und Lizenzierung ab dem 05.02.2024
Montag, März 4th, 2024 Produkte und Lizenzierung ab dem 05.02.2024
Produkte und Lizenzierung ab dem 05.02.2024
Keine vSphere Academic Lizenzen mehr
Nur noch Core Lizensierung möglich
Keinen VMware vSphere Free Hypervisor mehr
Keine VMware vSphere Perpetual Lizenzen mehr möglich
Keine VMware Renewal von Perpetual Lizenzen mehr möglich
Kein vSphere Essentials Bundle mehr
Neue vSAN Lizenzen nicht mehr mit Essentials Plus oder Standard Lizenzen
Aktuell keine Upgrade SKUs von Perpetual auf Subscription verfügbar
Aktuell kein CoTerm möglich
Nur noch disconnected Lizenzen
Keine Editionsupgrade SKUs vorhanden
Kombination vom Perpetual und Subscription Lizenzen möglich
Wer noch auf der VMware Schiene weiter unterwegs sein möchte oder muss hat die Möglichkeit folgende Produkte bei VMware oder Partnern zu ordern
- vSphere Essentials Plus Bundle (VVEP)
- vSphere Standard (VVS)
- vSphere Foundation (VVF)
- VMware Cloud Foundation (VCF)
Das Kürzel VVS steht für VMware Validated Solutions for Cloud Services Providers VCF steht für VMware Cloud Foundation und VVEP steht für VMware vSphere Essentials Plus Kit und VMware vSphere Foundation (VVF) ist eine neue Edition für KMU und bietet eine vereinfachte Workload Plattform auf Unternehmensniveau
VMware by Broadcom – End Of General Availability of the free vSphere Hypervisor (ESXi 7.x and 8.x)
Dienstag, Februar 13th, 2024 VMware by Broadcom – End of General Availability of the free vSphere Hypervisor (ESXi 7.x and 8.x)
VMware by Broadcom – End of General Availability of the free vSphere Hypervisor (ESXi 7.x and 8.x)
XCP-ng 8.2.1 – exploring from a VMware user’s perspective
Sonntag, Februar 4th, 2024Dell – hat seinen Vertrag mit VMware offiziell beendet der es dem Unternehmen erlaubte, die Virtualisierungsprodukte von VMware eigenständig weiter zu vertreiben
Mittwoch, Januar 31st, 2024
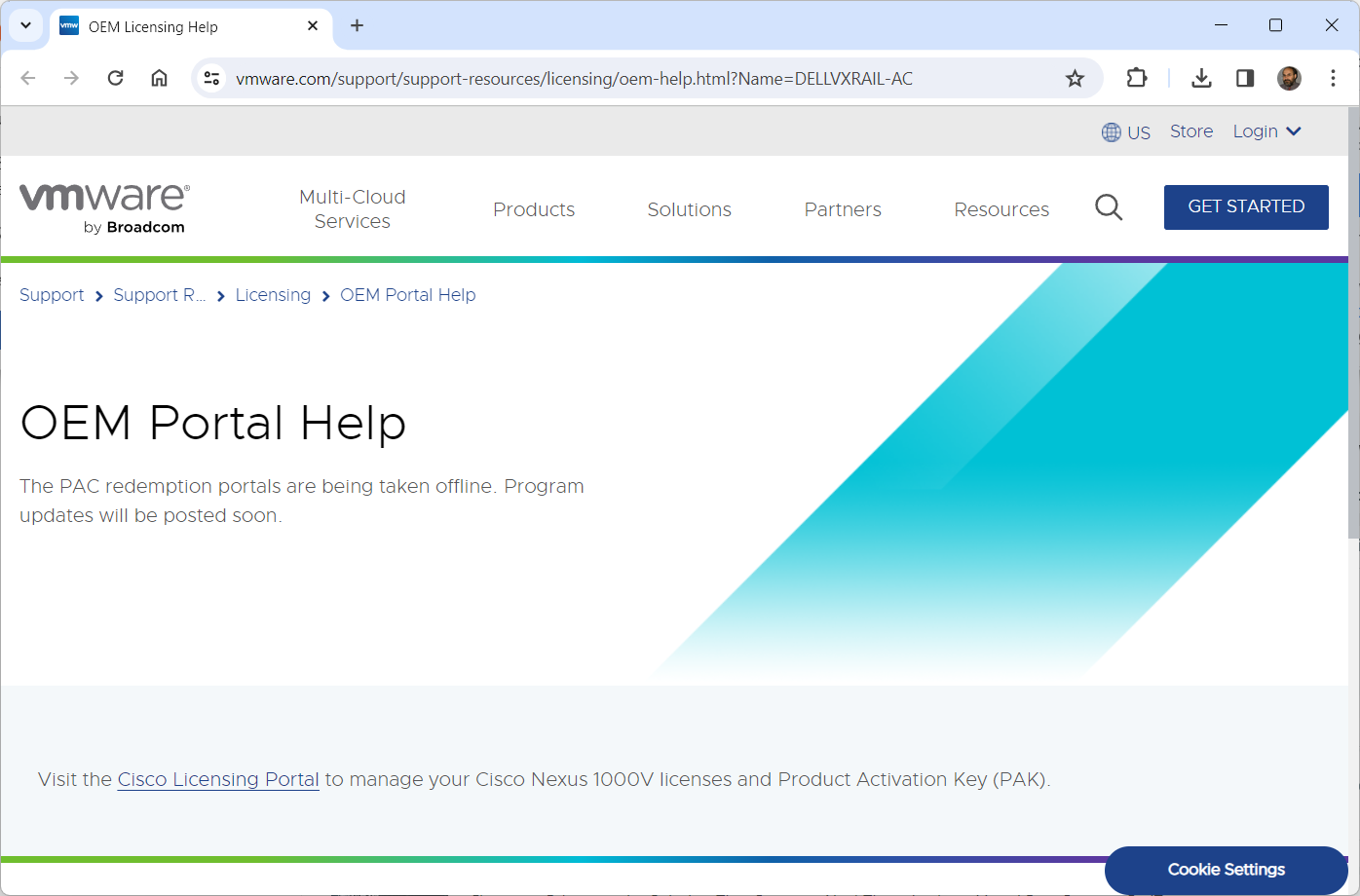
VMware OEM Portal – is offline and customers cannot activate their VMware licenses
Freitag, Januar 12th, 2024Broadcom President and CEO Hock Tan – Hands VMware Partners ‘Termination Notice’
Sonntag, Dezember 24th, 2023![]() Existing VMware partner agreements will be canceled by Broadcom on February 4 and partners must apply now to discover if they will be permitted to continue selling VMware By Broadcom one source said partners making below $ 500.000 in annual VMware revenue are in danger of losing their partner status
Existing VMware partner agreements will be canceled by Broadcom on February 4 and partners must apply now to discover if they will be permitted to continue selling VMware By Broadcom one source said partners making below $ 500.000 in annual VMware revenue are in danger of losing their partner status