Anwendungen am besten selbst untersuchen mit
Archive for Dezember 12th, 2021
Log4j Exploit – die Sicherheitslücke erklärt
Sonntag, Dezember 12th, 2021# find / -name log4j-core-*.jar
GoPro – Best of 2021
Sonntag, Dezember 12th, 2021Sonntag, Dezember 12th, 2021
Aufgrund der Sicherheitslücke #log4j wurden präventiv zum Schutz von Patientendaten einige Dienste der #Telematikinfrastruktur vom Internet getrennt. Wir arbeiten zusammen mit unseren Partnern mit Hochdruck daran. Updates: https://t.co/qI9knTEKYc#BSI
— gematik (@gematik1) December 12, 2021
Latte v0 – can isolate and measure network latency while excluding other types of latency such as application latency
Sonntag, Dezember 12th, 2021 Latte – for accurate network latency testing of the protocols used by most applications SockPerf (for Linux) and Latte (for Windows) produce the most relevant results
Latte – for accurate network latency testing of the protocols used by most applications SockPerf (for Linux) and Latte (for Windows) produce the most relevant results
Allow Latte through the Windows firewall
C:\>netsh advfirewall firewall add rule program=C:\PC_TOOLS\LattePortable\latte.exe name=“latte“ protocol=any dir=in action=allow enable=yes profile=ANY
Run latency tests
On the receiver start latte.exe (run it from the CMD window not from PowerShell)
latte -a <Receiver IP address>:<port> -i <iterations>
Around 65000 iterations is long enough to return representative results
Any available port number is fine.
If the VM has an IP address of 10.0.0.4 the command would look like this
C:\>PC_TOOLS\LattePortable\latte.exe -a 192.168.27.105:5005 -i 65100
On the sender start latte.exe (run it from the CMD window not from PowerShell)
latte -c -a <Receiver IP address>:<port> -i <iterations>
The resulting command is the same as on the receiver except with the addition of -c to indicate that this is the client or sender
C:\>PC_TOOLS\LattePortable\latte.exe -c -a 192.168.127.105:5005 -i 65100
Note that both commands include the same IP@ the address of the receiver
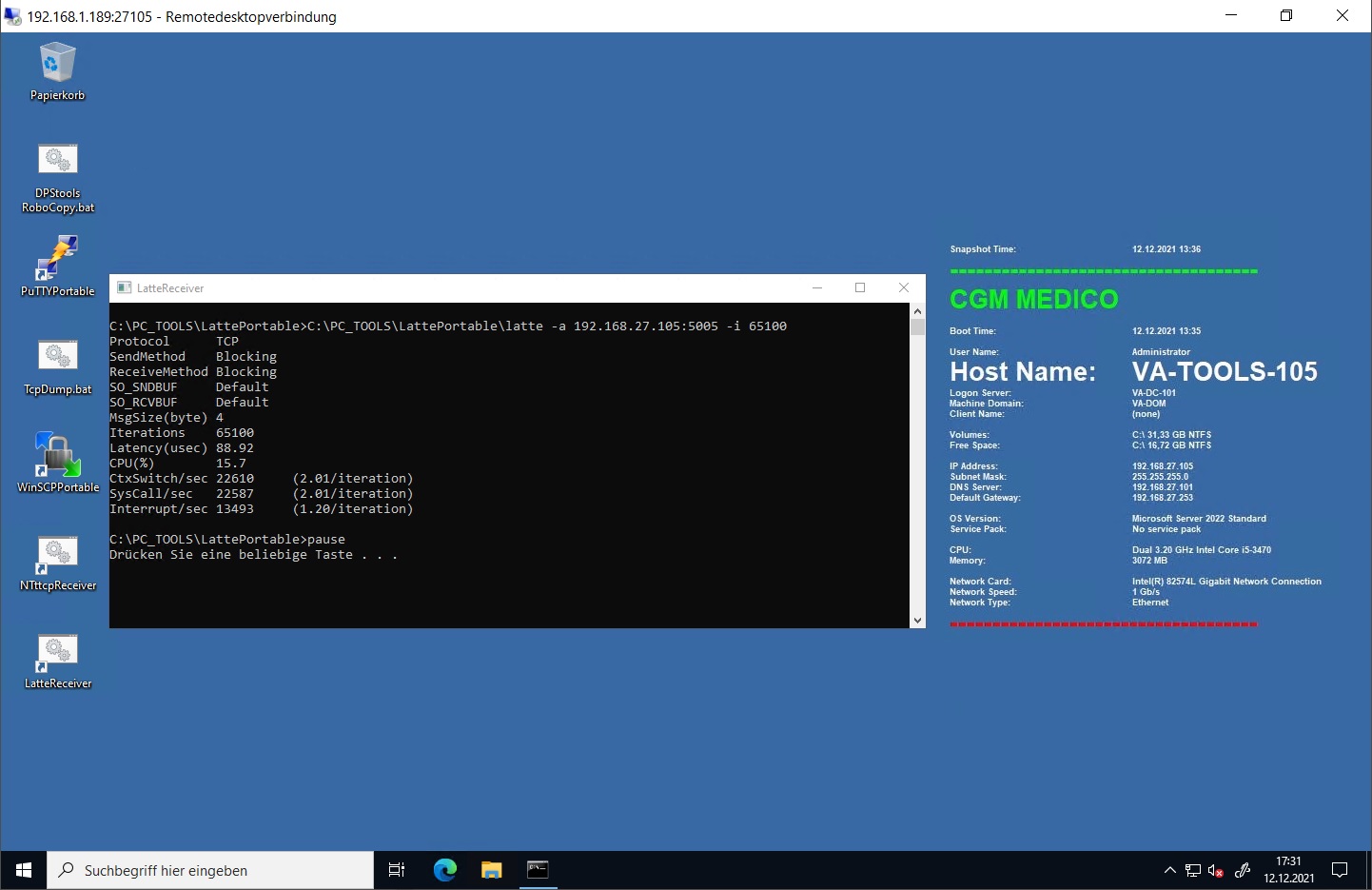
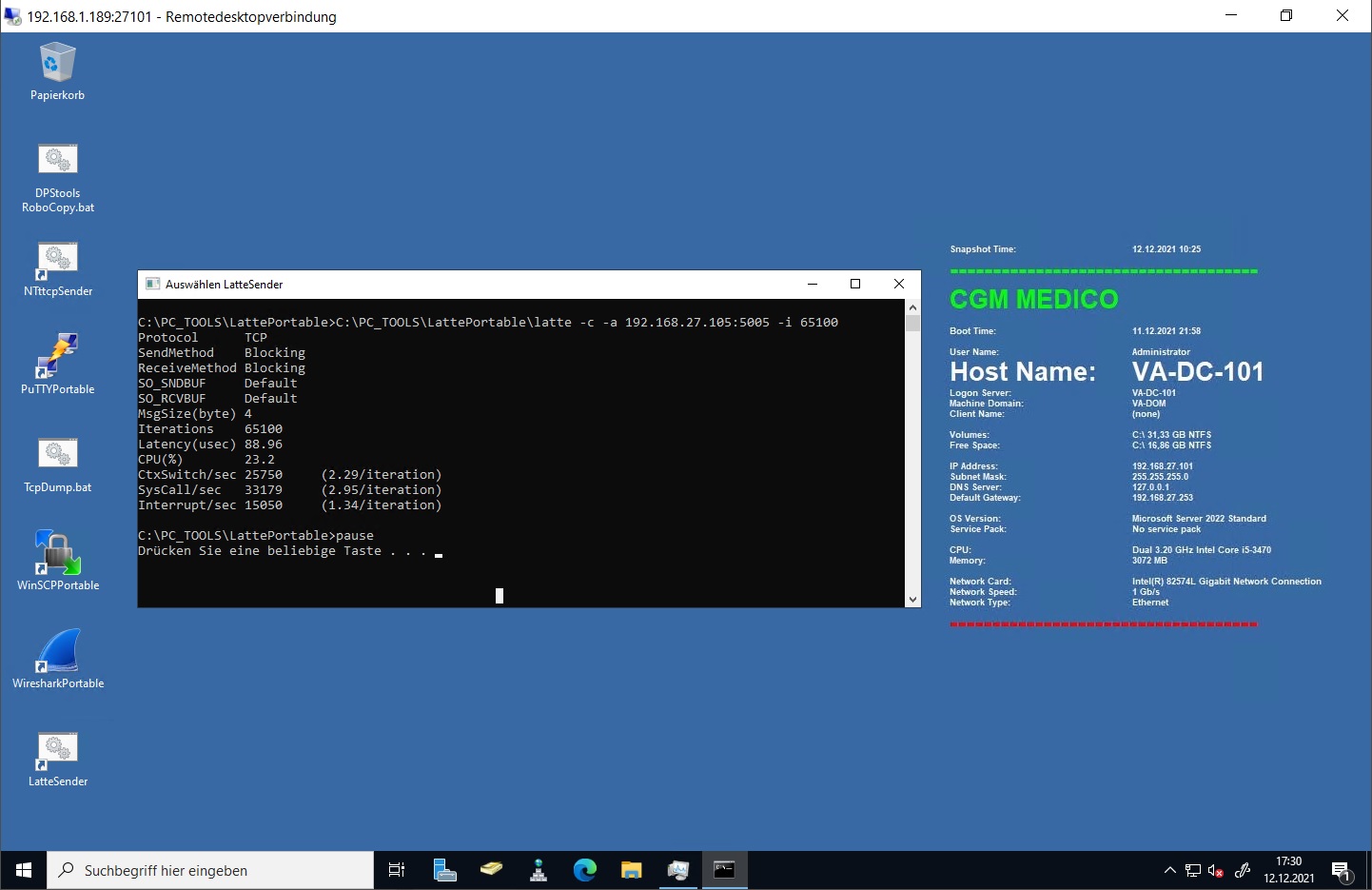
I ran the test fives times and the lowest latency score I received with my default setup was a latency of 89 usec (microseconds) – that’s 89 millionths of a second
Pössl H-Line Concorde Compact – seit vielen Jahren einen Klassiker
Sonntag, Dezember 12th, 2021Prof. Dr. Edmund Weitz – Mathematische Eleganz hoch drei
Sonntag, Dezember 12th, 2021Sonntag, Dezember 12th, 2021
The new drivers of modern object storage: it is not just cost https://t.co/yCQhAnA4pX
— MinIO (@Minio) December 11, 2021
Sonntag, Dezember 12th, 2021
Die Aufzeichnung unserer Online Veranstaltung "Jahresvorschau 2022" vom 01.12. ist nun auf YouTube verfügbar. Dort finden Sie Infos zu Anwendungen der #TI und einen Ausblick auf die Digitalisierung im Gesundheitswesen: https://t.co/mzWgw1hzSw #gematik
— gematik (@gematik1) December 12, 2021
NTttcp v5.38 – a Windows network throughput benchmark tool
Sonntag, Dezember 12th, 2021 NTttcp – when troubleshooting network performance issues it can be difficult to isolate network performance from that of other system components. When testing performance by copying a file from one system to another for example the memory and disk subsystems on both machines are being utilized to read from one machine and write to the other as well as the network. Fortunately there is a tool available from Microsoft specifically designed to test only the network
NTttcp – when troubleshooting network performance issues it can be difficult to isolate network performance from that of other system components. When testing performance by copying a file from one system to another for example the memory and disk subsystems on both machines are being utilized to read from one machine and write to the other as well as the network. Fortunately there is a tool available from Microsoft specifically designed to test only the network
NTttcp: [-s|-r|-l|-n|-p|-sp|-ns|-to|-a|-rb|-sb|-u|-w|-d|-t|-cd|-wu|-v|-6|-wa|-nic|-xml|-ndl|-na|-hpt|-uso|-uro] -m <mappings>
-s work as a sender
-r work as a receiver
-l <Length of buffer> [default TCP: 64K, UDP: 128]
-n <Number of buffers> [default: 20K]
-p <port base> [default: 5001]
-a <outstanding I/O> [default: 2]
-rb <Receive buffer size> [default: -1]
-ndl set TCP_NODELAY socket option
-u UDP send/recv
-w WSARecv/WSASend
-rt enable roundtrip mode
-d Verify Flag
-t <Runtime> in seconds
-v enable verbose mode
-6 enable IPv6 mode
-m <mappings>
Allow NTttcp through the Windows firewall
C:\>netsh advfirewall firewall add rule program=C:\PC_TOOLS\NTttcpPortable\ntttcp.exe name=“ntttcp“ protocol=any dir=in action=allow enable=yes profile=ANY
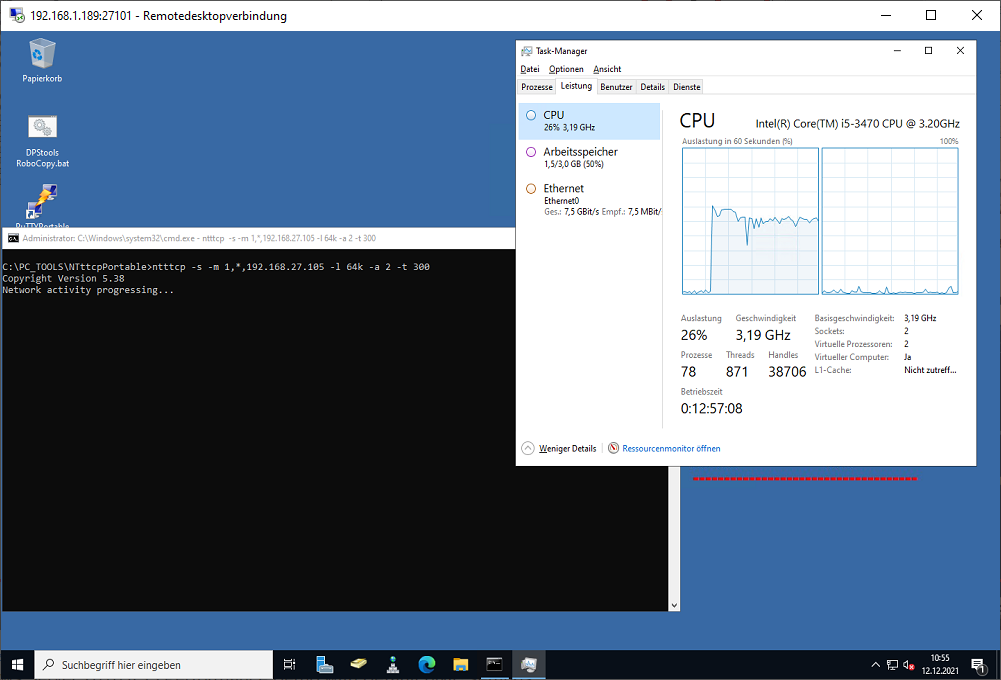
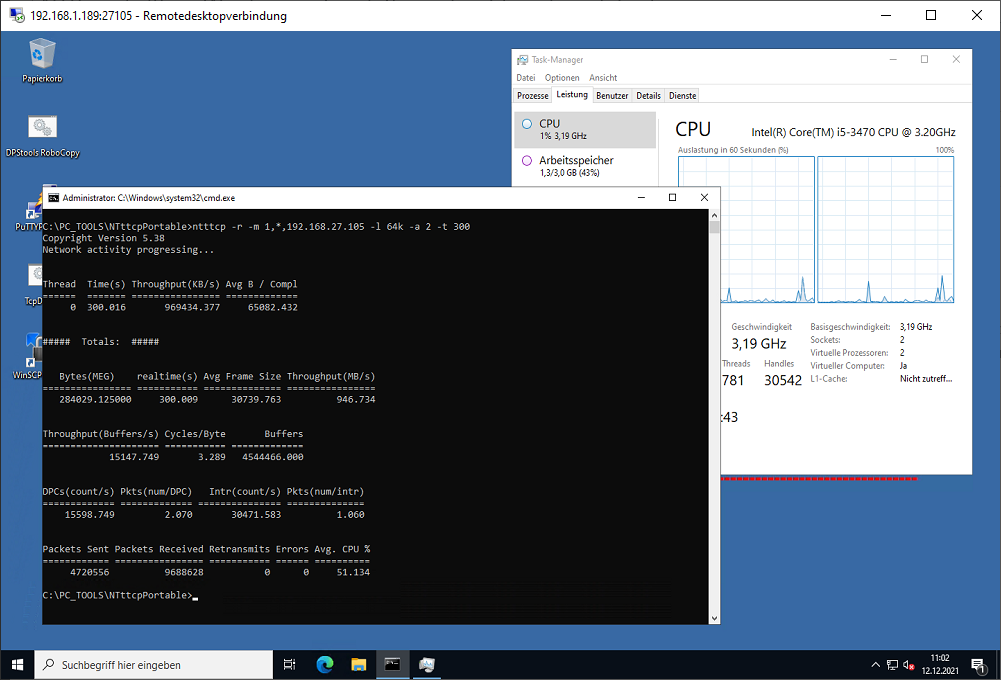
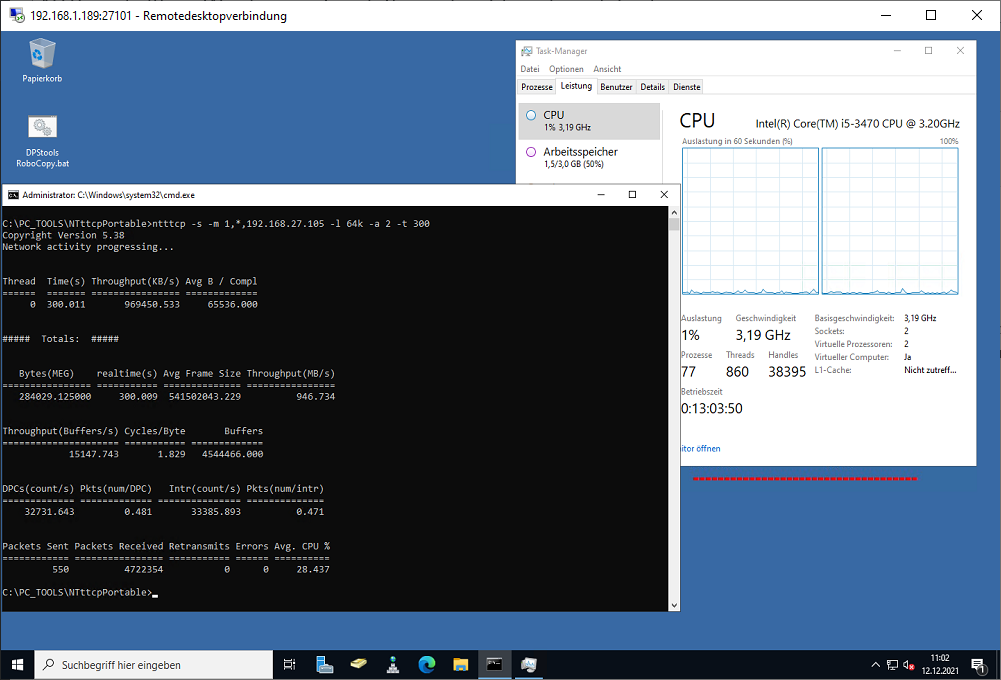
Running NTttcp tests
Start NTttcp on the RECEIVER (run from CMD not from PowerShell)
ntttcp -r –m [2*#num_cores],*,a.b.c.r -t 300
If the VM has four cores and an IP address of 10.0.0.4, it would look like this
C:\>PC_TOOLS\NTttcpPortable\ntttcp -r –m 1,*,192.168.27.105 -t 300
Start NTttcp on the SENDER (run from CMD not from PowerShell)
C:\>PC_TOOLS\NTttcpPortable\ntttcp -s –m 1,*,192.168.27.105 -t 300
Note that both commands include the same IP@ the address of the receiver
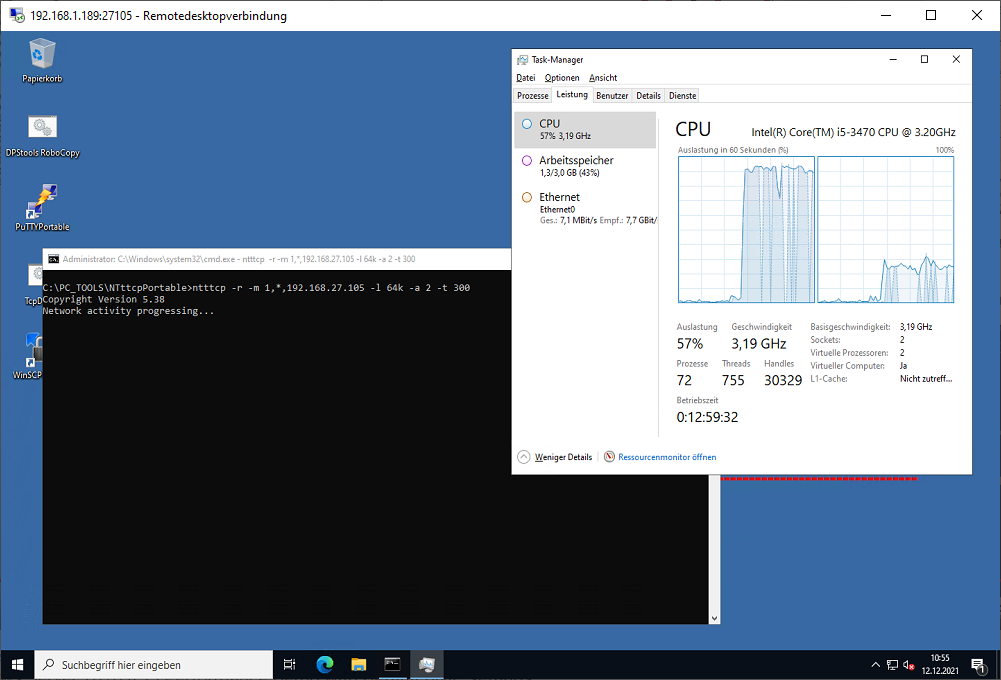
Phishing Kampagne – mit „Hilfe“ von Google
Sonntag, Dezember 12th, 2021Bundesamt für Sicherheit in der Informationstechnik (BSI) – Schwachstelle Log4Shell führt zu extrem kritischer Bedrohungslage
Sonntag, Dezember 12th, 2021Almost all versions of Log4j are vulnerable starting from 2.0-beta9 to 2.14.1 – the simplest and most effective protection method is to install the most recent version of the library 2.15.0
Sonntag, Dezember 12th, 2021You can download it on the project page
AVM FRITZ!Tech – USB Stick im Windows Explorer anzeigen lassen
Sonntag, Dezember 12th, 2021Sonntag, Dezember 12th, 2021
Das BSI stuft seine Warnmeldung zu #log4j auf Warnstufe Rot hoch. Unternehmen und Organisationen sollten Abwehrmaßnahmen schnellstmöglich umsetzen und Detektions- und Reaktionsfähigkeiten erhöhen. Mehr dazu unter: https://t.co/Xx7CoLIyln #DeutschlandDigitalSicherBSI #log4shell
— BSI (@BSI_Bund) December 11, 2021
