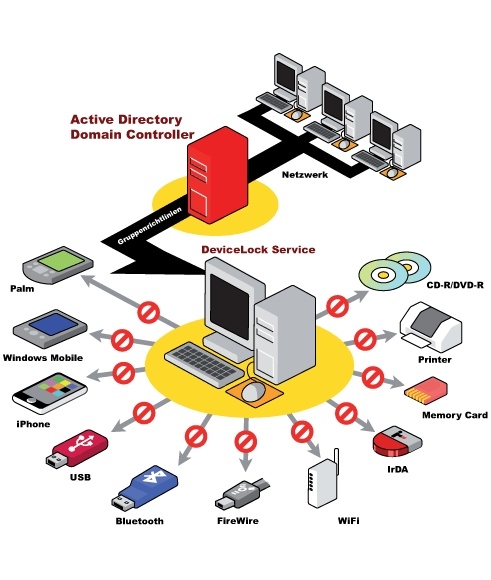
The data you are striving to protect behind firewalls and passwords is likely still slipping through your fingers. For every lost or stolen laptop or backup tape that makes it into the headlines, consider the many unreported, undocumented data leaks that occur when proprietary information is copied by either unwitting employees or users with malicious intent from their PCs to flash memory sticks, cell phones, cameras, PDAs, or other convenient forms of portable storage
The data you are striving to protect behind firewalls and passwords is likely still slipping through your fingers. For every lost or stolen laptop or backup tape that makes it into the headlines, consider the many unreported, undocumented data leaks that occur when proprietary information is copied by either unwitting employees or users with malicious intent from their PCs to flash memory sticks, cell phones, cameras, PDAs, or other convenient forms of portable storage