![]() VMware vSphere ESXi 6.x/7.x Hypervisor(s) – both CVE-2019-5544 and CVE-2020-3992 vulnerabilities in VMware ESXi impact the Service Location Protocol (SLP) reside in the OpenSLP open-source implementation of the Service Location Protocol (SLP) which allows the software to locate resources on a network
VMware vSphere ESXi 6.x/7.x Hypervisor(s) – both CVE-2019-5544 and CVE-2020-3992 vulnerabilities in VMware ESXi impact the Service Location Protocol (SLP) reside in the OpenSLP open-source implementation of the Service Location Protocol (SLP) which allows the software to locate resources on a network
Archive for the ‘VMware vSphere 7’ Category
VMware vSphere ESXi 6.x/7.x Hypervisor(s) – Ransomware operators are exploiting two vulnerabilities CVE-2019-5544 and CVE-2020-3992 to encrypt virtual hard disks
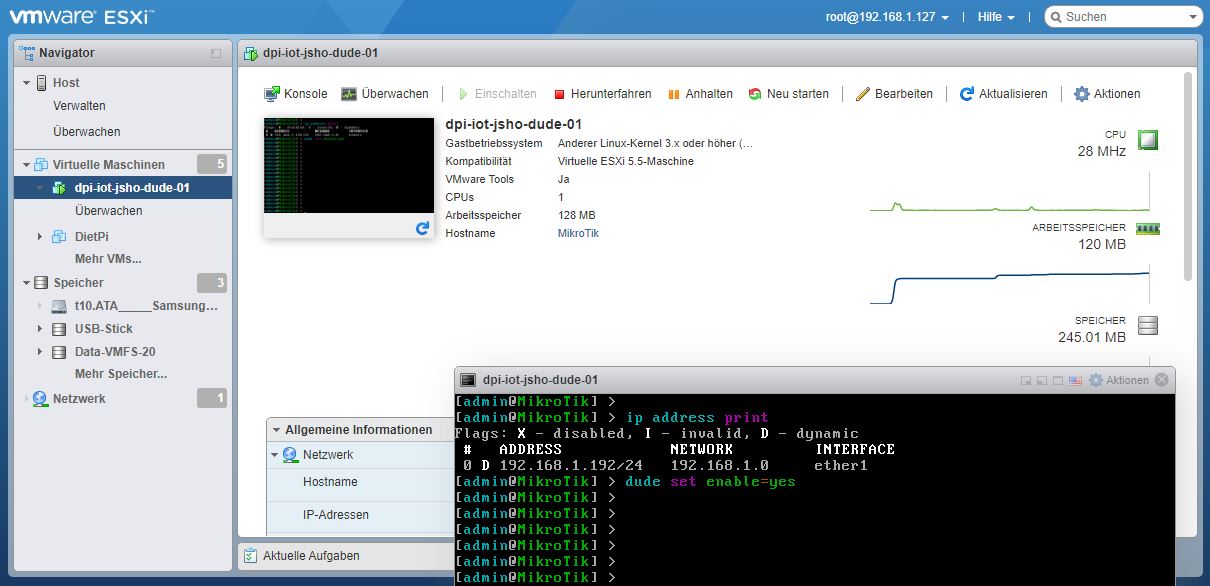
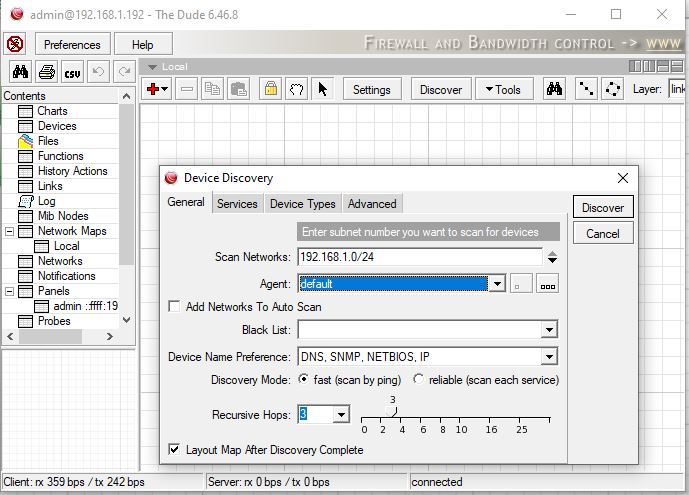
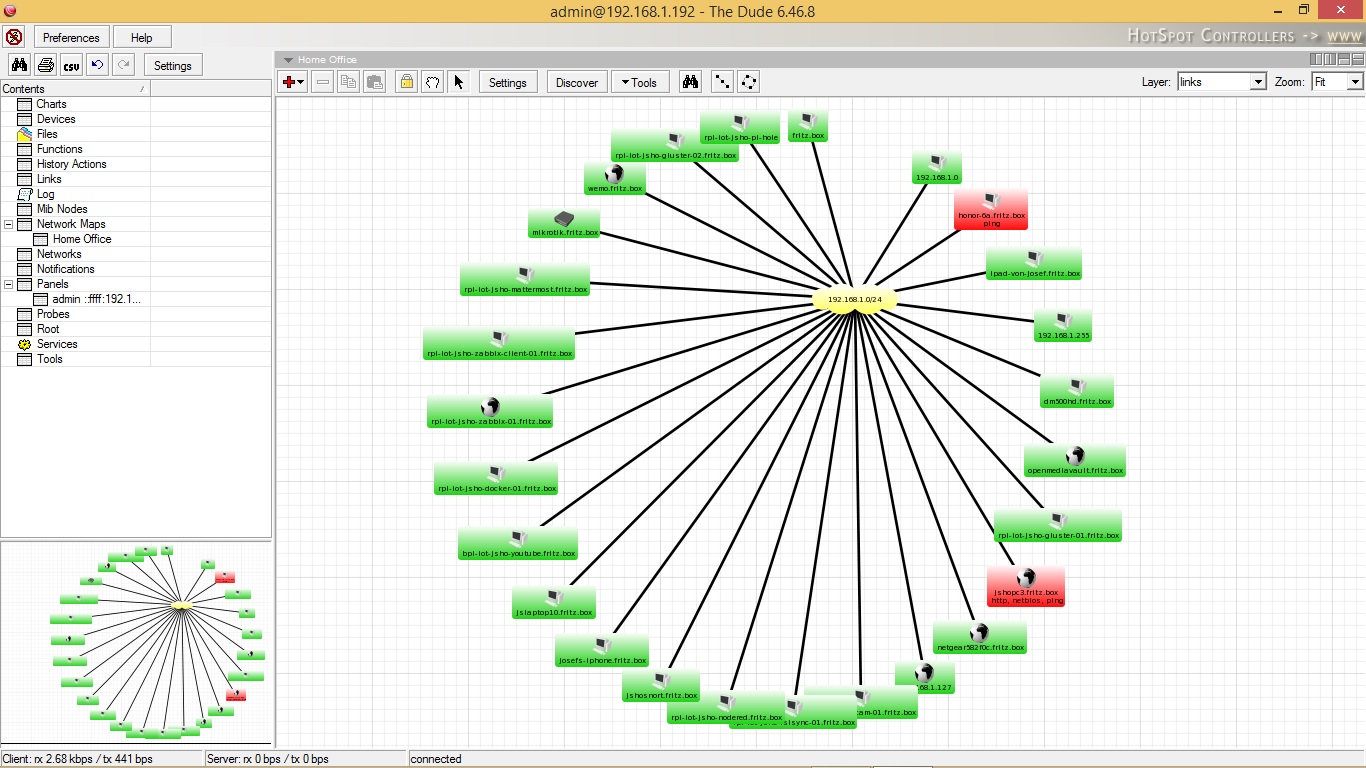
Dienstag, Februar 2nd, 2021VMware vSphere ESXi 7.0 Hypervisor(s) – Dude 6.46.8 Server Installation
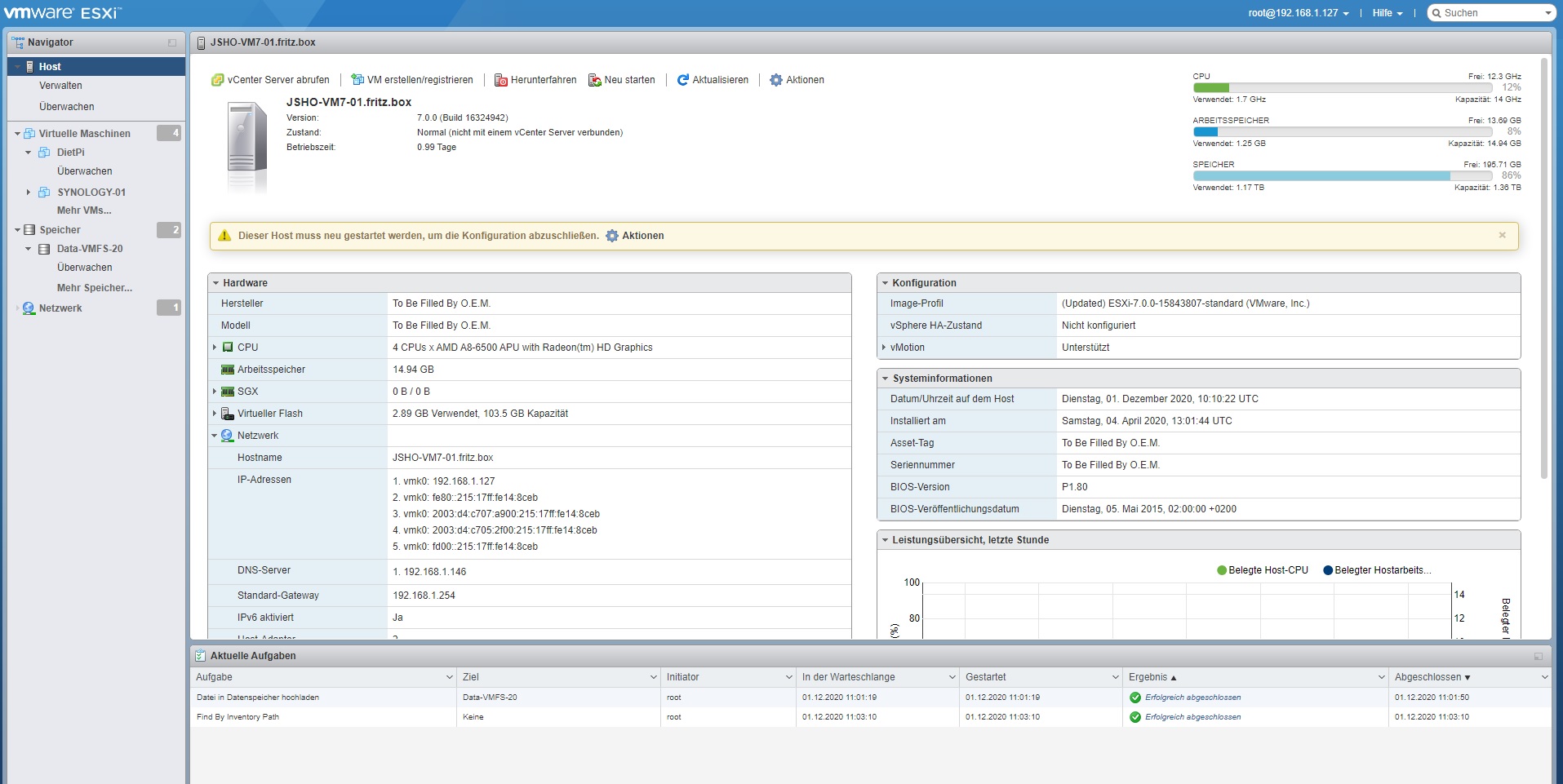
Donnerstag, Dezember 24th, 2020VMware vSphere ESXi 7.0 Hypervisor(s) – manually attach USB Device as a VMFS Datastore
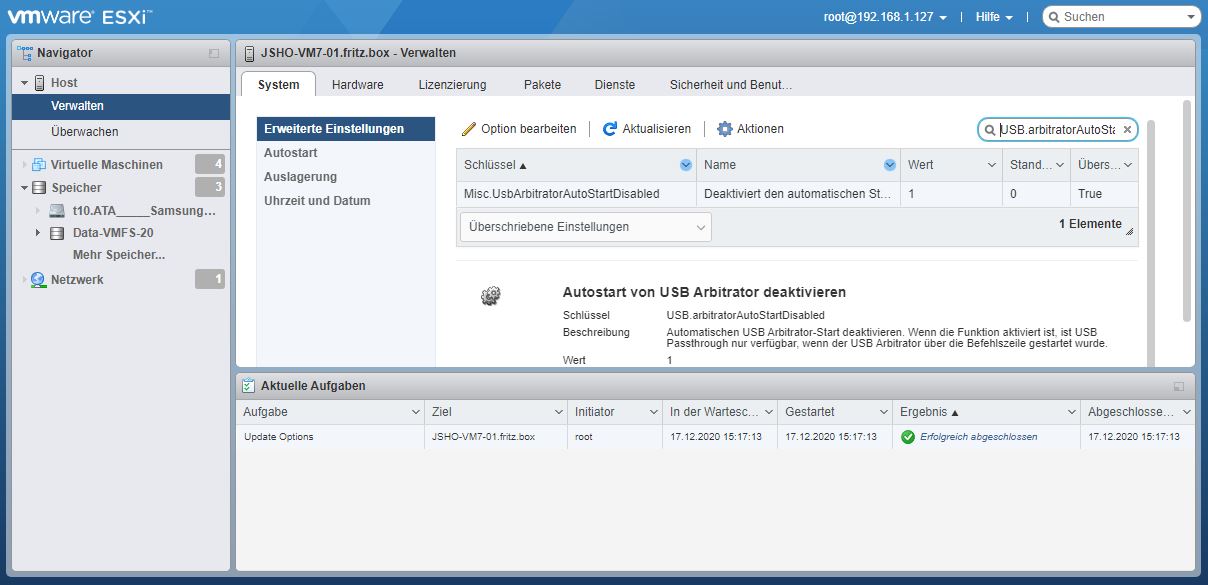
Freitag, Dezember 18th, 2020![]() Stop the USB arbitrator service – this service is used to passthrough USB device from an ESXi host to a virtual machine but when disabling it you can no longer passthrough USB devices to VMs
Stop the USB arbitrator service – this service is used to passthrough USB device from an ESXi host to a virtual machine but when disabling it you can no longer passthrough USB devices to VMs

[root@JSHO-VM7-01:~] ls /dev/disks/
mpx.vmhba32:C0:T0:L0 vml.010000000020202020202047544630303250414b4d48583746486974616368
t10.ATA_____Hitachi_HDS721010KLA330_______________________GTF002PAKMHX7F vml.0100000000323133303237323738393430506f72746162
t10.ATA_____Hitachi_HDS721010KLA330_______________________GTF002PAKMHX7F:1 vml.0100000000323133303237323738393430506f72746162:1
t10.ATA_____KINGSTON_SA400S37120G___________________50026B77821FCF81____ vml.010000000035303032364237373832314643463831202020204b494e475354
t10.ATA_____KINGSTON_SA400S37120G___________________50026B77821FCF81____:1 vml.010000000035303032364237373832314643463831202020204b494e475354:1
t10.ATA_____KINGSTON_SA400S37120G___________________50026B77821FCF81____:5 vml.010000000035303032364237373832314643463831202020204b494e475354:5
t10.ATA_____KINGSTON_SA400S37120G___________________50026B77821FCF81____:6 vml.010000000035303032364237373832314643463831202020204b494e475354:6
t10.ATA_____KINGSTON_SA400S37120G___________________50026B77821FCF81____:7 vml.010000000035303032364237373832314643463831202020204b494e475354:7
t10.ATA_____Samsung_SSD_850_EVO_500GB_______________S2RBNXAH334538W_____ vml.0100000000533252424e58414833333435333857202020202053616d73756e
t10.ATA_____Samsung_SSD_850_EVO_500GB_______________S2RBNXAH334538W_____:1 vml.0100000000533252424e58414833333435333857202020202053616d73756e:1
[root@JSHO-VM7-01:~] partedUtil mklabel /dev/disks/mpx.vmhba32\:C0\:T0\:L0 gpt
[root@JSHO-VM7-01:~] eval expr $(partedUtil getptbl /dev/disks/mpx.vmhba32\:C0\:T0\:L0 | tail -1 | awk ‚{print $1 “ \\* “ $2 “ \\* “ $3}‘) – 1
976768064
[root@JSHO-VM7-01:~] partedUtil showGuids
Partition Type GUID
vmfs AA31E02A400F11DB9590000C2911D1B8
vmkDiagnostic 9D27538040AD11DBBF97000C2911D1B8
vsan 381CFCCC728811E092EE000C2911D0B2
virsto 77719A0CA4A011E3A47E000C29745A24
VMware Reserved 9198EFFC31C011DB8F78000C2911D1B8
Basic Data EBD0A0A2B9E5443387C068B6B72699C7
Linux Swap 0657FD6DA4AB43C484E50933C84B4F4F
Linux Lvm E6D6D379F50744C2A23C238F2A3DF928
Linux Raid A19D880F05FC4D3BA006743F0F84911E
Efi System C12A7328F81F11D2BA4B00A0C93EC93B
Microsoft Reserved E3C9E3160B5C4DB8817DF92DF00215AE
Unused Entry 00000000000000000000000000000000
[root@JSHO-VM7-01:~] partedUtil setptbl /dev/disks/mpx.vmhba32\:C0\:T0\:L0 gpt „1 2048 976768064 AA31E02A400F11DB9590000C2911D1B8 0“
gpt
0 0 0 0
1 2048 976768064 AA31E02A400F11DB9590000C2911D1B8 0
[root@JSHO-VM7-01:~] vmkfstools -C vmfs5 -S USB-Stick /dev/disks/mpx.vmhba32\:C0\:T0\:L0:1
create fs deviceName:’/dev/disks/mpx.vmhba32:C0:T0:L0:1′, fsShortName:’vmfs5′, fsName:’USB-Stick‘
deviceFullPath:/dev/disks/mpx.vmhba32:C0:T0:L0:1 deviceFile:mpx.vmhba32:C0:T0:L0:1
ATS on device /dev/disks/mpx.vmhba32:C0:T0:L0:1: not supported
.
Checking if remote hosts are using this device as a valid file system. This may take a few seconds…
Creating vmfs5 file system on „mpx.vmhba32:C0:T0:L0:1“ with blockSize 1048576 and volume label „USB-Stick“.
Successfully created new volume: 5fdb5f37-a8d660b9-c730-001517148cea
[root@JSHO-VM7-01:~] ls /dev/disks/
mpx.vmhba32:C0:T0:L0 vml.010000000020202020202047544630303250414b4d48583746486974616368
mpx.vmhba32:C0:T0:L0:1 vml.010000000020202020202047544630303250414b4d48583746486974616368:1
t10.ATA_____Hitachi_HDS721010KLA330_______________________GTF002PAKMHX7F vml.0100000000323133303237323738393430506f72746162
t10.ATA_____Hitachi_HDS721010KLA330_______________________GTF002PAKMHX7F:1 vml.0100000000323133303237323738393430506f72746162:1
t10.ATA_____KINGSTON_SA400S37120G___________________50026B77821FCF81____ vml.010000000035303032364237373832314643463831202020204b494e475354
t10.ATA_____KINGSTON_SA400S37120G___________________50026B77821FCF81____:1 vml.010000000035303032364237373832314643463831202020204b494e475354:1
t10.ATA_____KINGSTON_SA400S37120G___________________50026B77821FCF81____:5 vml.010000000035303032364237373832314643463831202020204b494e475354:5
t10.ATA_____KINGSTON_SA400S37120G___________________50026B77821FCF81____:6 vml.010000000035303032364237373832314643463831202020204b494e475354:6
t10.ATA_____KINGSTON_SA400S37120G___________________50026B77821FCF81____:7 vml.010000000035303032364237373832314643463831202020204b494e475354:7
t10.ATA_____Samsung_SSD_850_EVO_500GB_______________S2RBNXAH334538W_____ vml.0100000000533252424e58414833333435333857202020202053616d73756e
t10.ATA_____Samsung_SSD_850_EVO_500GB_______________S2RBNXAH334538W_____:1 vml.0100000000533252424e58414833333435333857202020202053616d73756e:1
MinIO – the Object Storage on VMware Cloud Foundation with Tanzu using the vSAN Data Peristence platform
Mittwoch, Dezember 16th, 2020Oracle Real Application Cluster (RAC) – Support on VMware Clouds
Montag, Dezember 14th, 2020As of December 9th 2020 VMware recommends that anyone currently running OR planning to run, an Oracle Real Application Cluster (RAC) in a VMware Cloud environment reach out to Oracle Corporation for any Oracle support related matters with RAC on our cloud platform
Key points to keep in mind …
1) This guidance does NOT relate to or affect the technical feasibility of running Oracle RAC or the licensing of Oracle RAC in a VMware Cloud environment
2) This guidance does NOT pertain to running Oracle RAC in an on-premises VMware Software Defined Data Center as that remains unaffected. More on the Oracle on VMware Support Metalink Note 249212.1 can be found here
3) This guidance is based on recent changes to the “Oracle Real Application Clusters (RAC) Support on Third-Party Clouds – An Overview and Clarification – Revision 2020.06.14” Oracle document
MinIO – the Intersection of VMware and Cloud Native Storage
Donnerstag, Dezember 10th, 2020VMware OVF Tool – ‚Error: Fault cause: vim.fault.FileNotFound‘
Dienstag, Dezember 1st, 2020This error means that the VM has an ISO still connect to it – what you have to do is to go in the vSphere client and disconnect the ISO and after that the copying process will work

VMware vSphere ESXi 7.0 Hypervisor(s) – how to easily update your VMware Hypervisor from 7.0b Build 16324942 to 7.0U1b Build 17168206 using ESXCLI
Dienstag, Dezember 1st, 2020VMware vSphere ESXi 7.0 Hypervisor(s) – how to run Raspberry Pi OS as a VM on a Raspberry Pi
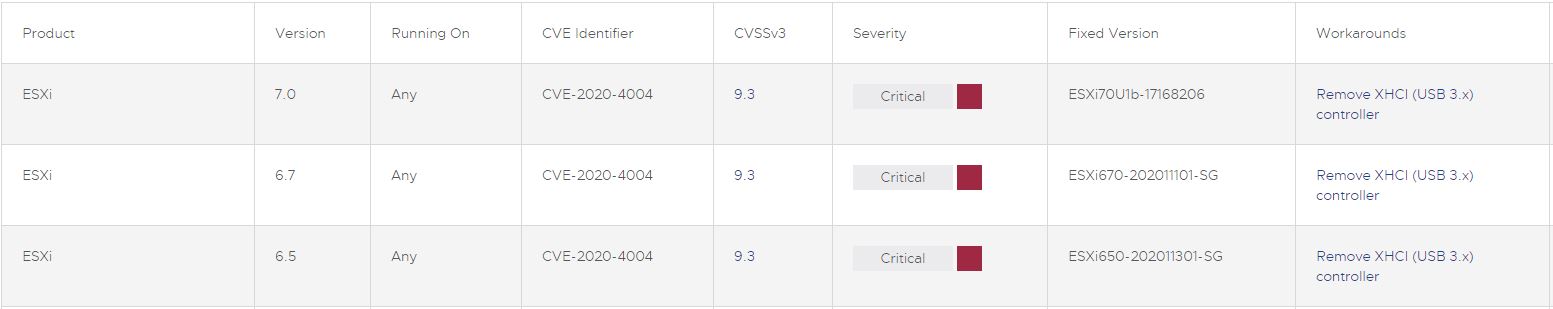
Samstag, November 28th, 2020VMware vSphere 6.x/7.x – contain a use-after-free vulnerability in the XHCI USB controller
Freitag, November 20th, 2020SAP ERP-System S/4 HANA – running on VMware vSphere 7.x
Samstag, Oktober 24th, 2020HPE ProLiant DL380 Gen9 Server – the HPE Dynamic Smart Array B140i Controller is not compliant with certain HPE Gen9 platforms running VMware ESXi 7.0
Samstag, Oktober 17th, 2020The HPE Dynamic Smart Array B140i Controller will not be listed on the compliance recipe list for VMware ESXi 7.0 because it is not supported on certain HPE Gen9 platforms running VMware ESXi 7.0
Raspberry Pi 4 8GB – boot a ESXi-ARM ISO
Mittwoch, Oktober 14th, 2020VMware vSphere 7 Update 1 – a quick look at new features
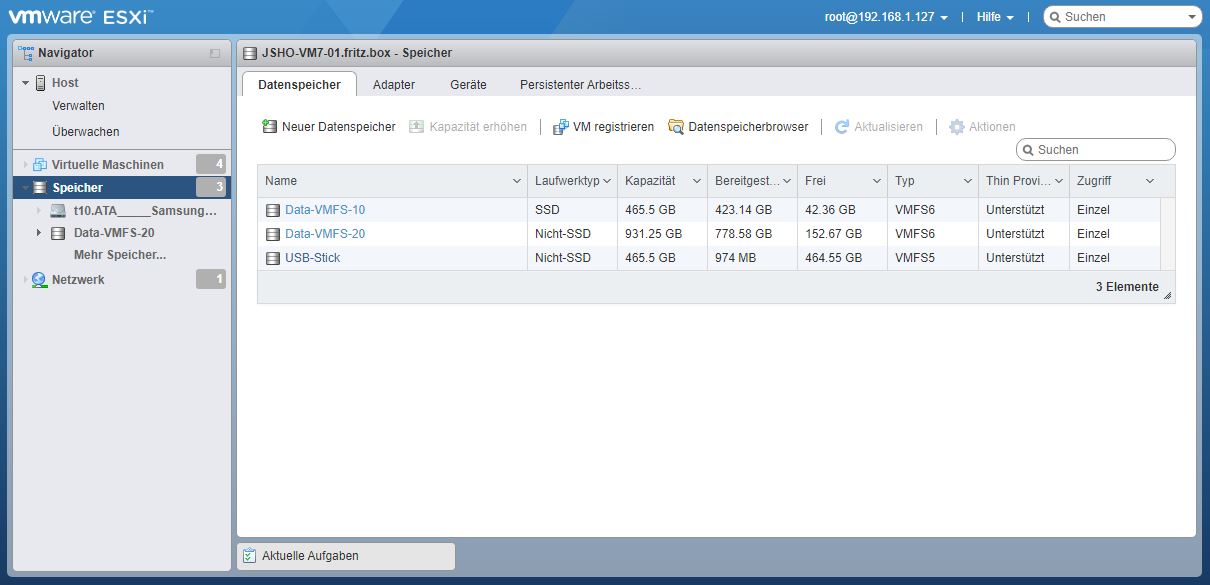
Freitag, September 25th, 2020VMware vSphere 7.0 – USB Devices as VMFS Datastore
Montag, September 21st, 2020![]() This article explains how to add USB devices as Datastores – adding USB devices as datastores was also possible in previous versions but in vSphere 7 it has become even easier
This article explains how to add USB devices as Datastores – adding USB devices as datastores was also possible in previous versions but in vSphere 7 it has become even easier