Archive for the ‘VMware vSphere 7’ Category
Linux version of Ransomware AvosLocker – targets VMware vSphere Hypervisor (ESXi 6.x/7.x)
Dienstag, Januar 11th, 2022VMware vSphere Hypervisor (ESXi 7.x) – CD-ROM vulnerability (CVE-2021-22045) the workaround requires that all CD-ROM/DVD devices are disabled/disconnected on all running virtual machines
Freitag, Januar 7th, 2022Microsoft Windows 11 – how to make your own virtual machine server with VMware ESXi
Sonntag, Dezember 12th, 2021VMware vSphere Hypervisor (ESXi 7.x) – automated installation
Sonntag, November 28th, 2021VMware vSphere 7.0 Update 3 – important information
Samstag, November 20th, 2021![]() VMware vSphere Blog – after careful consideration we have removed the ESXi 7 Update 3 release from our Product Downloads site
VMware vSphere Blog – after careful consideration we have removed the ESXi 7 Update 3 release from our Product Downloads site
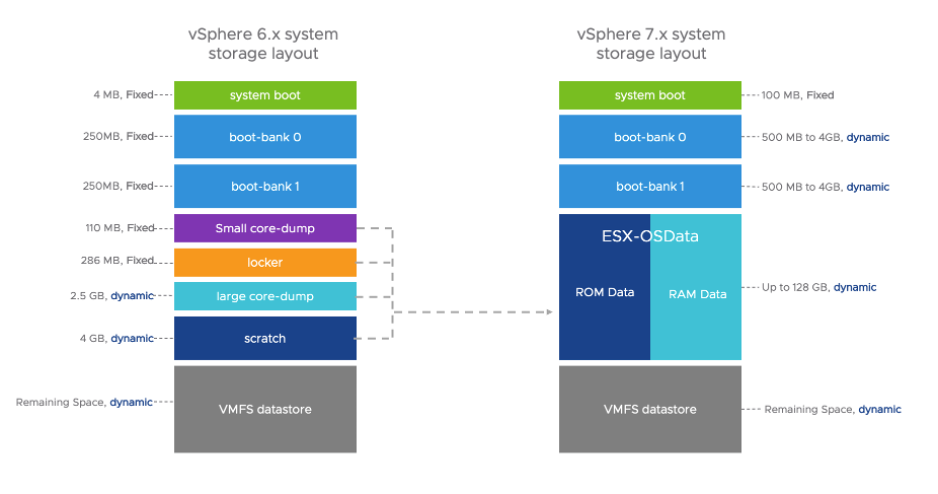
VMware vSphere Hypervisor (ESXi 7.x) – historically SD cards or USB devices have been chosen to free up device bays and lower the cost of installing ESXi hosts
Mittwoch, November 17th, 2021![]() VMware vSphere Hypervisor (ESXi 7.x) – Boot Media Considerations and VMware Technical Guidance
VMware vSphere Hypervisor (ESXi 7.x) – Boot Media Considerations and VMware Technical Guidance
VMware vCenter Server – Integrated Windows Authentication (IWA) privilege escalation vulnerability (CVE-2021-22048)
Samstag, November 13th, 2021Resolution – none
Workaround (86292) – for CVE-2021-22048 is to switch to AD over LDAPS authentication/Identity Provider Federation for AD FS (vSphere 7.0 only) from Integrated Windows Authentication (IWA)
SanDisk MAX ENDURANCE microSD Card – is engineered not only for continuous recording and re-recording but also for continuous peace of mind for years to come
Mittwoch, Oktober 27th, 2021

No future for booting ESXi from USB in VMware home labs using max endurance microSD for ESXi 7.0U3 now
VMware vSphere Hypervisor (ESXi 7.x) – Purple Screen Of Death (PSOD) after updating to vSphere ESXi 7.0 Update 3
Montag, Oktober 25th, 2021Symptoms:
Recent upgrade to ESXi 7.0.3 Build: 18644231
Thin provisioned virtual disks (VMDKs) residing on VMFS6 datastores may cause multiple hosts in an HA cluster to fail with a purple diagnostic screen
Resolution:
This is a known issue in VMware vSphere ESXi 7.0 Update 3 release currently there is no resolution. If you experience this issue please contact VMware support and reference this article
Workaround:
There are a few options that customers have to work around this issue. Please note that any of these workarounds will prevent the issue from happening customers only need to choose the workaround that is best for their situation
1. Revert to the previous version of ESXi that is not impacted by this concern https://kb.vmware.com/s/article/1033604
2. Convert thin VMDKs to Thick or EZT provisioning
Determine the Virtual Disk Format and Convert a Virtual Disk from the Thin Provision Format to a Thick Provision Format
https://docs.vmware.com/en/VMware-vSphere/7.0/com.vmware.vsphere.vm_admin.doc/GUID-E8F50BEC-F575-4AB1-BC77-D9A13CDBDCF7.html
3. Disable TRIM/UNMAP in the Guest OS
Please consult OS documentation on how to adjust TRIM/UNMAP features for a complete understanding of the OS specific configurations needs. Note: functions and capabilities may vary across distributions and versions based on OS specifics
Microsoft Power BI Desktop – merging RVTools reports
Sonntag, Oktober 10th, 2021 Microsoft Power BI Desktop – merging RVTools reports
Microsoft Power BI Desktop – merging RVTools reports
VMware vSphere Hypervisor (ESXi 7.x) – installing or removing packages fails with „BOOTx64.EFI not found“ error
Freitag, Oktober 8th, 2021![]() VMware vSphere Hypervisor (ESXi 7.x) – installing or removing packages fails with „BOOTx64.EFI not found“ error
VMware vSphere Hypervisor (ESXi 7.x) – installing or removing packages fails with „BOOTx64.EFI not found“ error
Python ransomware script targets ESXi server for encryption – because configuration errors rapidly escalated to a ransomware attack inside a virtual machine hypervisor
Mittwoch, Oktober 6th, 2021![]() Securing the ESXi Hypervisor – by default the ESXi Shell and SSH services are not running and only the root user can log in to the Direct Console User Interface (DCUI) if you decide to enable ESXi or SSH access you can set timeouts to limit the risk of unauthorized access
Securing the ESXi Hypervisor – by default the ESXi Shell and SSH services are not running and only the root user can log in to the Direct Console User Interface (DCUI) if you decide to enable ESXi or SSH access you can set timeouts to limit the risk of unauthorized access
VMware has also published a list of best practices for administrators of their ESXi hypervisors on how to secure them and limit the attack surface on the hypervisor itself