Archive for the ‘Network Info’ Category
What happens if there is no DHCP server – how do devices communicate with each other
Donnerstag, Juni 5th, 2025MikroTik Dude – provides an application that allows you to monitor your network
Dienstag, Juni 3rd, 2025AVM FRITZ!Tech – der Fritz!Repeater 1610 Outdoor ist für den Außeneinsatz nach IP54 zertifiziert
Dienstag, Juni 3rd, 2025Progress Kemp LoadMaster – weshalb der Citrix ADC (NetScaler) nicht immer die beste Wahl ist
Montag, Juni 2nd, 20251&1 Glasfaser – einen Anschluss vorbereiten und aktivieren
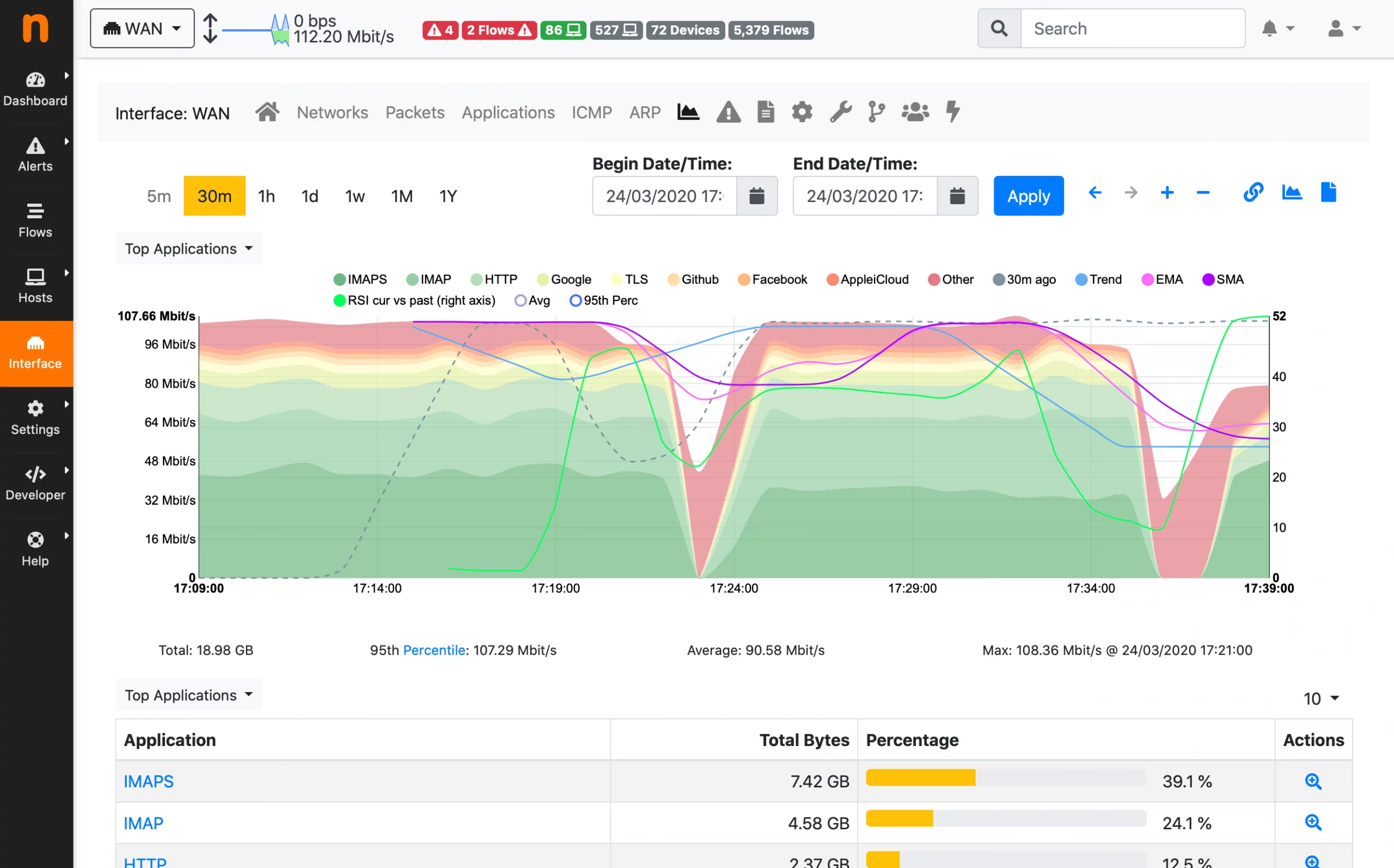
Donnerstag, Mai 29th, 2025ntopng – showcasing practical real world scenarios where ntopng can be effectively utilized
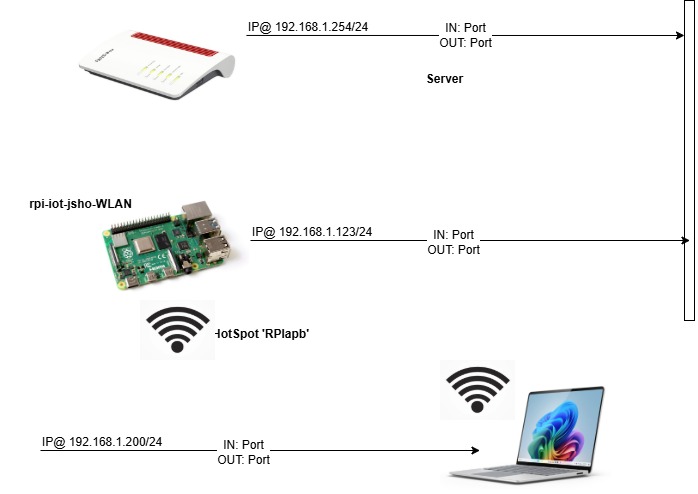
Dienstag, Mai 27th, 2025Raspberry Pi – setting up Network Manager for a Wi-Fi Access Point act as a Hotspot (bridging mode)
Sonntag, Mai 25th, 2025root@rpi-iot-jsho-WLAN:~# nmcli device disconnect wlan0
root@rpi-iot-jsho-WLAN:~# nmcli device up wlan0
root@rpi-iot-jsho-WLAN:~# nmcli connection add type ethernet slave-type bridge con-name ‚Ethernet‘ ifname eth0 master bridge0
root@rpi-iot-jsho-WLAN:~# nmcli connection add type bridge con-name ‚Bridge‘ ifname bridge0
Network Management Command-Line Interface ’nmcli‘ is a powerful tool for managing network connections on Linux systems using Network Manager and it allows users to view modify and manage network settings e.g. ’nmcli connection add con-name ‚Hotspot‘ ifname <DEVICE> type wifi slave-type bridge master bridge0 wifi.mode ap wifi.ssid <SSID> wifi-sec.key-mgmt wpa-psk wifi-sec.proto rsn wifi-sec.pairwise ccmp wifi-sec.psk <PASSWORD>‘
root@rpi-iot-jsho-WLAN:~# nmcli connection add con-name ‚Hotspot‘ ifname wlan0 type wifi slave-type bridge master bridge0 wifi.mode ap wifi.ssid RPIapb wifi-sec.key-mgmt wpa-psk wifi-sec.proto rsn wifi-sec.pairwise ccmp wifi-sec.psk password
root@rpi-iot-jsho-WLAN:~# nmcli connection up Bridge
root@rpi-iot-jsho-WLAN:~# nmcli connection up Hotspot
root@rpi-iot-jsho-WLAN:~# nmcli dev wifi show-password
SSID: RPIapb
Security: WPA
Password: password

root@rpi-iot-jsho-WLAN:~#
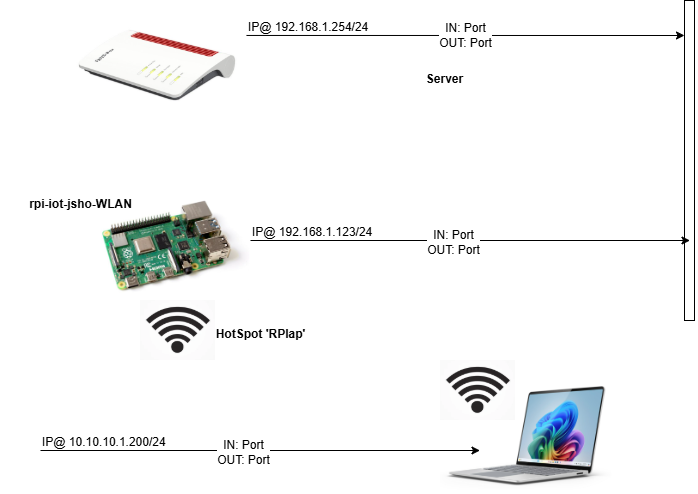
Raspberry Pi – setting up Network Manager for a Wi-Fi Access Point act as a Hotspot (routing mode)
Samstag, Mai 24th, 2025root@rpi-iot-jsho-WLAN:~#
root@rpi-iot-jsho-WLAN:~# apt-get install network-manager
Reading package lists… Done
Building dependency tree… Done
Reading state information… Done
network-manager is already the newest version (1.42.4-1+rpt1+deb12u1).
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
root@rpi-iot-jsho-WLAN:~#
Network Management Command-Line Interface ’nmcli‘ is a powerful tool for managing network connections on Linux systems using Network Manager and it allows users to view modify and manage network settings e.g. ’nmcli d wifi hotspot ifname <DEVICE> ssid <SSID> password <PASSWORD>‘
root@rpi-iot-jsho-WLAN:~# nmcli d wifi hotspot ifname wlan0 ssid RPIap password password
Device ‚wlan0‘ successfully activated with ‚1101fb4d-372e-4e57-9fb4-10b0bc20626c‘.
Hint: „nmcli dev wifi show-password“ shows the Wi-Fi name and password.
root@rpi-iot-jsho-WLAN:~# nmcli dev wifi show-password
SSID: RPIap
Security: WPA
Password: password

root@rpi-iot-jsho-WLAN:~#
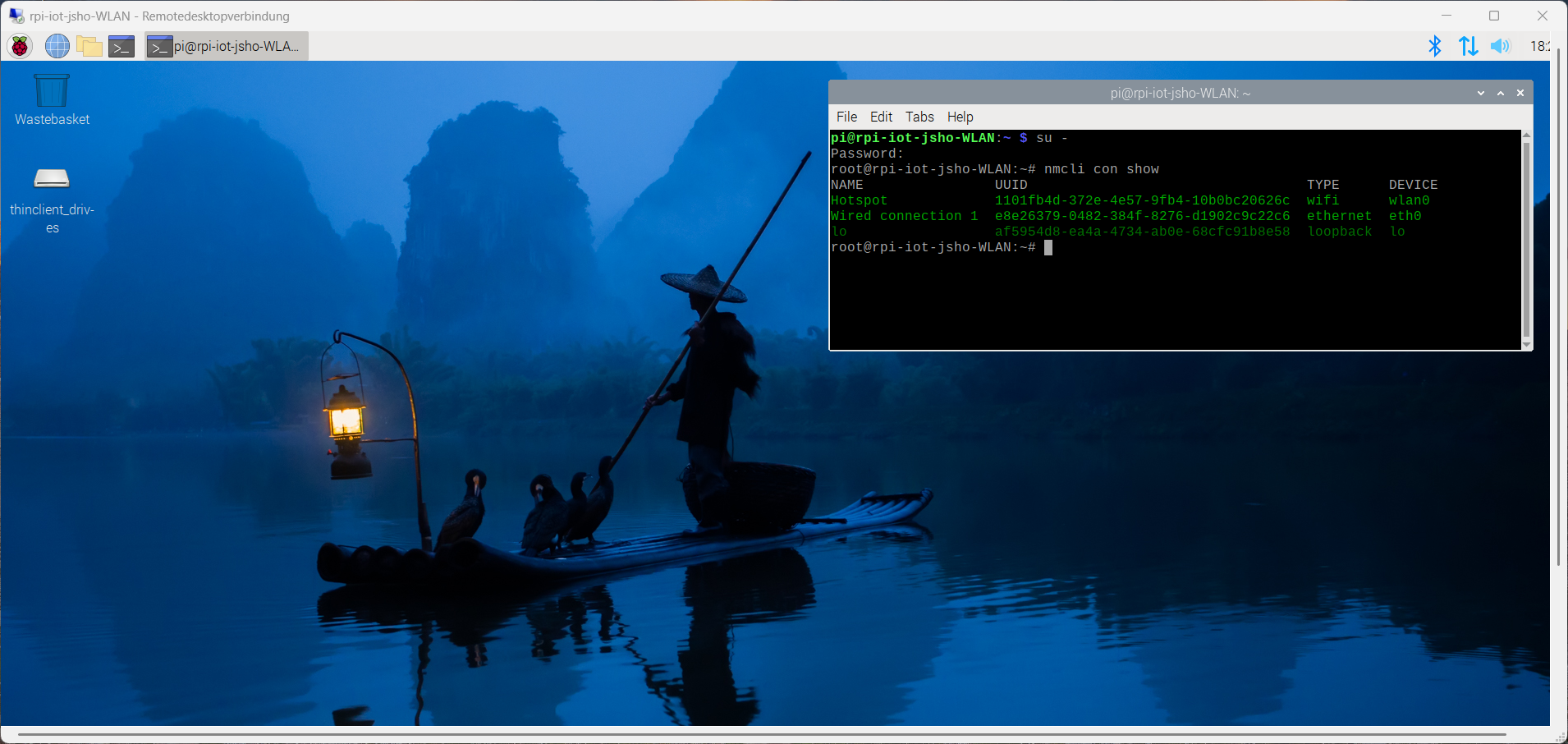
root@rpi-iot-jsho-WLAN:~# nmcli con show
NAME UUID TYPE DEVICE
Hotspot 1101fb4d-372e-4e57-9fb4-10b0bc20626c wifi wlan0
Wired connection 1 e8e26379-0482-384f-8276-d1902c9c22c6 ethernet eth0
lo af5954d8-ea4a-4734-ab0e-68cfc91b8e58 loopback lo
root@rpi-iot-jsho-WLAN:~#
Docusnap 14 – VLAN einfach erklärt
Donnerstag, Mai 22nd, 2025AVM FRITZ!Tech – wie lange hält die Batterie des intelligenten Stromsensors FRITZ!Smart Energy 250
Donnerstag, Mai 22nd, 2025Nmap & Zenmap – Schwachstellen finden im Home Lab
Montag, Mai 19th, 2025root@js-FUTRO-S740:~# apt-get install zenmap
root@js-FUTRO-S740:~# zenmap –version
zenmap 7.95

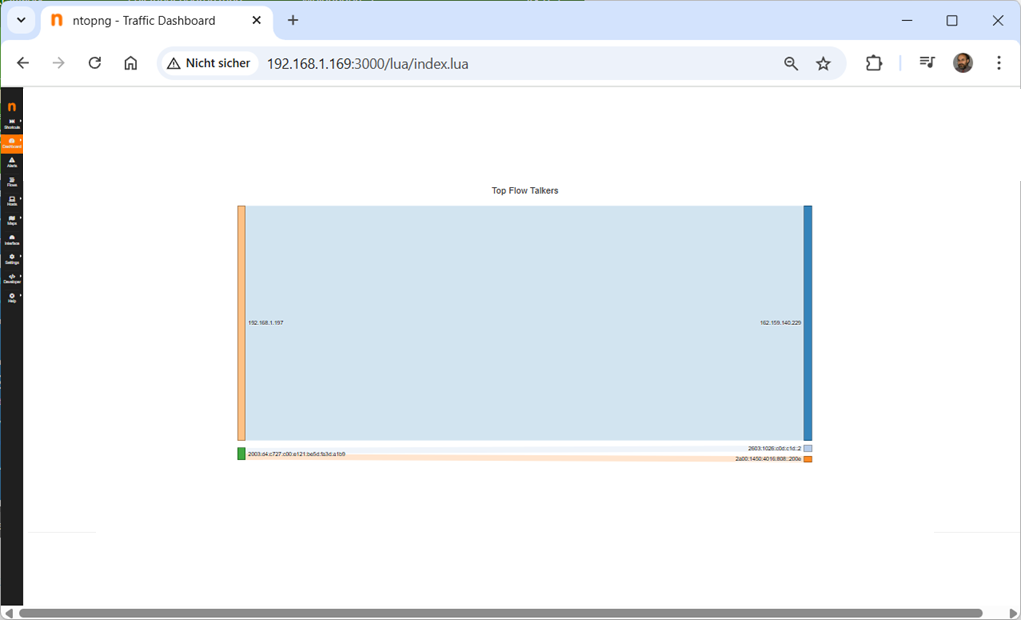
FRITZ!Box Packet Sniffer – Netzwerk Traffic direkt mit der FRITZ!Box aufzeichnen und mit ‚Ntopng‘ online auswerten
Dienstag, Mai 13th, 2025root@js-FUTRO-S740:~# apt-get install ntopng
root@js-FUTRO-S740:~# vi FritzBoxPacketSniffer
#!/bin/bash
set -x
# This is the address of the router
FRITZIP=http://IP@
# This is the WAN interface
IFACE=“2-0″
# Lan Interface
#IFACE=“1-lan“
# If you use password-only authentication use ‚dslf-config‘ as username.
FRITZUSER=<user>
FRITZPWD=<password>
SIDFILE=“/tmp/fritz.sid“
if [ -z „$FRITZPWD“ ] || [ -z „$FRITZUSER“ ] ; then echo „Username/Password empty. Usage: $0 <username> <password>“ ; exit 1; fi
echo „Trying to login into $FRITZIP as user $FRITZUSER“
if [ ! -f $SIDFILE ]; then
touch $SIDFILE
fi
SID=$(cat $SIDFILE)
# Request challenge token from Fritz!Box
CHALLENGE=$(curl -k -s $FRITZIP/login_sid.lua | grep -o „<Challenge>[a-z0-9]\{8\}“ | cut -d‘>‘ -f 2)
# Very proprieatry way of AVM: Create a authentication token by hashing challenge token with password
HASH=$(perl -MPOSIX -e ‚
use Digest::MD5 „md5_hex“;
my $ch_Pw = „$ARGV[0]-$ARGV[1]“;
$ch_Pw =~ s/(.)/$1 . chr(0)/eg;
my $md5 = lc(md5_hex($ch_Pw));
print $md5;
‚ — „$CHALLENGE“ „$FRITZPWD“)
curl -k -s „$FRITZIP/login_sid.lua“ -d „response=$CHALLENGE-$HASH“ -d ‚username=’${FRITZUSER} | grep -o „<SID>[a-z0-9]\{16\}“ | cut -d‘>‘ -f 2 > $SIDFILE
SID=$(cat $SIDFILE)
# Check for successfull authentification
if [[ $SID =~ ^0+$ ]] ; then echo „Login failed. Did you create & use explicit Fritz!Box users?“ ; exit 1 ; fi
echo „Capturing traffic on Fritz!Box interface $IFACE …“ 1>&2
# How to use ntopng
# To ensure that ntopng resolves all numeric IPs, you would use the following command: ntopng –dns-mode 1
wget –no-check-certificate -qO- $FRITZIP/cgi-bin/capture_notimeout?ifaceorminor=$IFACE\&snaplen=\&capture=Start\&sid=$SID | ntopng –dns-mode 1 -i –