 Wireshark 4.4.7 – release notes
Wireshark 4.4.7 – release notes
Archive for the ‘Security Solution’ Category
Wireshark 4.4.7 Portable – the current stable release
Dienstag, Juni 10th, 2025Google Chrome OS Version 137.0.7151.69 – steht zum Download bereit
Dienstag, Juni 3rd, 2025Google Chrome OS Version 137.0.7151.41 – steht zum Download bereit
Montag, Mai 26th, 2025Bundesamtes für Sicherheit in der Informationstechnik (BSI) Präsidentin Claudia Plattner – wenn wir jetzt nicht handeln laufen wir in das Risiko dass Angreifer unsere Infrastruktur schwächen
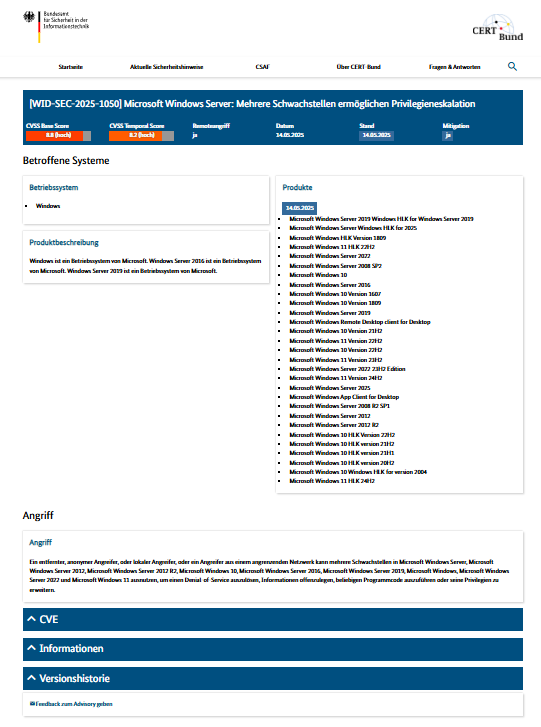
Sonntag, Mai 25th, 2025Bundesamt für Sicherheit in der Informationstechnik (BSI) – Microsoft bestätigt eine kritische Zero-Day-Schwachstelle in Windows (CVE-2025-30397) die aktiv von Angreifern ausgenutzt wird
Freitag, Mai 16th, 2025Google Chrome OS Version 136.0.7103.114 – steht zum Download bereit
Donnerstag, Mai 15th, 2025Home Lab 2025 – generate self signed certificates with OpenSSL to secure your servers
Mittwoch, Mai 14th, 2025Certificate Authority
Generate the Certificate Authority (CA) Private Key
Every certificate must have a corresponding private key. Generate this using the following command line
# openssl ecparam -name prime256v1 -genkey -noout -out ca.key
This will create a 256-bit private key over an elliptic curve, which is the industry standard. We know that Curve25519 is considered safer than this NIST P-256 curve but it is only standardized in TLS 1.3 which is not yet widely supported
Generate the Certificate Authority Certificate
The CA generates and issues certificates. Here is a link to additional resources if you wish to learn more about this.
Generate the Root CA certificate using the following command line
# openssl req -new -x509 -sha256 -key ca.key -out ca.crt
You will be prompted to provide some information about the CA. Here is what the request looks like:
You are about to be asked to enter information that will be incorporated into your certificate request
What you are about to enter is what is called a Distinguished Name or a DN
Country Name (2 letter code) [AU]:CA
State or Province Name (full name) [Some-State]:QC
Locality Name (eg, city) []:Lavaltrie
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Devolutions inc.
Organizational Unit Name (eg, section) []:Security
Common Name (e.g. server FQDN or YOUR name) []:devolutions.net
Email Address []:security@devolutions.net
Your CA certificate is now created. Keep its private key in a safe place
Generate your server certificate
This step may be repeated for each server you need
Generate the server certificate private key
Like the CA certificate use the following command line
# openssl ecparam -name prime256v1 -genkey -noout -out server.key
This will create a file name server.key
Understanding Snort Rules – the FritzBox sends ICMPv6 packets to distribute information about the network such as router announcements used for automatic address configuration (SLAAC) and DNS server discovery specifically ICMPv6 type 134 packets as routing advertisement with multicast address FF02:: are used to announce that the FritzBox is a router and provide information about available network prefixes and DNS servers
Mittwoch, Mai 7th, 202505/07-20:01:05.468282 [**] [1:10000001:1] ICMP test detected [**] [Classification: Generic ICMP event] [Priority: 3] {IPV6-ICMP} :: -> ff02::1:ff02:13ed

root@rpi-iot-jsho-snort-02:~# vi .swatchrc
ignore /ff02::/
watchfor /Priority\: [1-3]/
echo=normal
mail=js@dpsolution.de,subject=[SNORT] Priority [1-3] Alert
Snort 2.9.15.1 – network intrusion detection system (NIDS) installation & config & logging & rule writing
Mittwoch, Mai 7th, 2025![]()
root@rpi-iot-jsho-snort-02:~# apt-get install snort
root@rpi-iot-jsho-snort-02:~# snort -V
,,_ -*> Snort! <*-
o“ )~ Version 2.9.15.1 GRE (Build 15125)
““ By Martin Roesch & The Snort Team: http://www.snort.org/contact#team
Copyright (C) 2014-2019 Cisco and/or its affiliates. All rights reserved.
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using libpcap version 1.10.3 (with TPACKET_V3)
Using PCRE version: 8.39 2016-06-14
Using ZLIB version: 1.2.13
root@rpi-iot-jsho-snort-02:~#
root@rpi-iot-jsho-snort-02:~# systemctl status snort
● snort.service – LSB: Lightweight network intrusion detection system
Loaded: loaded (/etc/init.d/snort; generated)
Active: active (running) since Mon 2025-04-28 20:02:47 CEST; 21min ago
Docs: man:systemd-sysv-generator(8)
Tasks: 2 (limit: 383)
CPU: 11.421s
CGroup: /system.slice/snort.service
└─1570 /usr/sbin/snort -m 027 -D -d -l /var/log/snort -u snort -g snort –pid-path /run/snort/ -c /etc/snort/snort.conf -S „\“HOME_N>
Apr 28 20:02:47 rpi-iot-jsho-snort-02 snort[1570]: Preprocessor Object: SF_DNP3 Version 1.1 <Build 1>
Apr 28 20:02:47 rpi-iot-jsho-snort-02 snort[1570]: Preprocessor Object: SF_DNS Version 1.1 <Build 4>
Apr 28 20:02:47 rpi-iot-jsho-snort-02 snort[1570]: Preprocessor Object: SF_SMTP Version 1.1 <Build 9>
Apr 28 20:02:47 rpi-iot-jsho-snort-02 snort[1570]: Preprocessor Object: SF_SDF Version 1.1 <Build 1>
Apr 28 20:02:47 rpi-iot-jsho-snort-02 snort[1570]: Preprocessor Object: SF_IMAP Version 1.0 <Build 1>
Apr 28 20:02:47 rpi-iot-jsho-snort-02 snort[1570]: Preprocessor Object: SF_POP Version 1.0 <Build 1>
Apr 28 20:02:47 rpi-iot-jsho-snort-02 snort[1570]: Preprocessor Object: SF_SSH Version 1.1 <Build 3>
Apr 28 20:02:47 rpi-iot-jsho-snort-02 snort[1570]: Preprocessor Object: SF_GTP Version 1.1 <Build 1>
Apr 28 20:02:47 rpi-iot-jsho-snort-02 snort[1570]: Preprocessor Object: appid Version 1.1 <Build 5>
Apr 28 20:02:47 rpi-iot-jsho-snort-02 snort[1570]: Commencing packet processing (pid=1570)
root@rpi-iot-jsho-snort-02:~#
root@rpi-iot-jsho-snort-02:~# netstat -i
Kernel Interface table
Iface MTU RX-OK RX-ERR RX-DRP RX-OVR TX-OK TX-ERR TX-DRP TX-OVR Flg
eth0 1500 22633 0 56 0 4279 0 0 0 BMRU
lo 65536 38 0 0 0 38 0 0 0 LRU
root@rpi-iot-jsho-snort-02:~# ip link set eth0 promisc on
root@rpi-iot-jsho-snort-02:~# netstat -i
Kernel Interface table
Iface MTU RX-OK RX-ERR RX-DRP RX-OVR TX-OK TX-ERR TX-DRP TX-OVR Flg
eth0 1500 22873 0 56 0 4330 0 0 0 BMPRU
lo 65536 38 0 0 0 38 0 0 0 LRU
The flag will be updated to BMPRU
Flag details are as follows
B flag is for broadcast
M flag is for multicast
P flag is for promisc mode
R is for running
U is for up
root@rpi-iot-jsho-snort-02:~#
root@rpi-iot-jsho-snort-02:/etc/network# dmesg | tail -n 4
[ 87.654916] Bluetooth: HCI socket layer initialized
[ 87.654962] Bluetooth: L2CAP socket layer initialized
[ 87.655034] Bluetooth: SCO socket layer initialized
[ 108.558206] smsc95xx 1-1.1:1.0 eth0: entered promiscuous mode
Google Chrome OS Version 136.0.7103.93 – steht zum Download bereit
Mittwoch, Mai 7th, 2025Understanding Snort Rules – ‚alert udp any any -> any 67‘ Message „Possible DHCP server“ will alert if a TCP packet is sent from any source to any destination on port 67 potentially indicating a DHCP server this rule can be used to identify and alert on potential DHCP server activity on the network
Mittwoch, Mai 7th, 202505/07-10:15:17.565258 [**] [1:527:8] BAD-TRAFFIC same SRC/DST [**] [Classification: Potentially Bad Traffic] [Priority: 2] {UDP} 0.0.0.0:68 -> 255.255.255.255:67

root@rpi-iot-jsho-snort-02:~# vi .swatchrc
ignore /0.0.0.0:68 -> 255.255.255.255:67/
watchfor /Priority\: [1-3]/
echo=normal
mail=js@dpsolution.de,subject=[SNORT] Priority [1-3] Alert
Oettinger Brauerei – die in Bayern beheimatete Brauerei ist Opfer eines Ransomware Angriffs geworden
Mittwoch, Mai 7th, 2025
Understanding Snort Rules – the IP@ 239.255.255.250 is a multicast address and is used in conjunction with the Simple Service Discovery Protocol (SSDP) and SSDP is a protocol used to search for Universal Plug and Play (UPnP) devices in a network
Dienstag, Mai 6th, 202505/06-17:58:18.513849 [**] [1:1917:6] SCAN UPnP service discover attempt [**] [Classification: Detection of a Network Scan] [Priority: 3] {UDP} 192.168.1.167:1900 -> 239.255.255.250:1900
05/07-10:29:42.163512 [**] [1:1384:8] MISC UPnP malformed advertisement [**] [Classification: Misc Attack] [Priority: 2] {UDP} 2003:d4:c71d:ba00:3e37:12ff:fe55:1452:1900 -> ff0e::c:1900