A remote code execution vulnerability exists in Remote Desktop Services formerly known as Terminal Services – when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests. This vulnerability is pre-authentication and requires no user interaction. An attacker who successfully exploited this vulnerability could execute arbitrary code on the target system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights
A remote code execution vulnerability exists in Remote Desktop Services formerly known as Terminal Services – when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests. This vulnerability is pre-authentication and requires no user interaction. An attacker who successfully exploited this vulnerability could execute arbitrary code on the target system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights
Archive for the ‘Windows Server 2019’ Category
Microsoft Windows 7/8 & Windows Server W2k8/W2k12/W2k16/W2k19 – CVE-2019-1182 | Remote Desktop Services Remote Code Execution Vulnerability Security Vulnerability
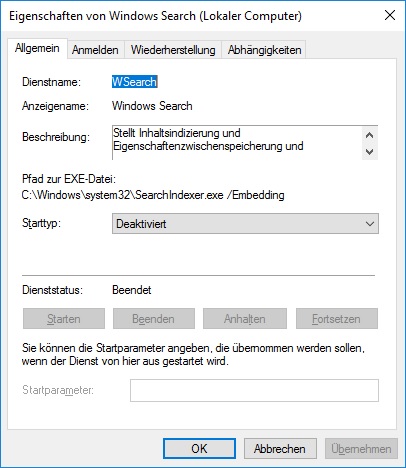
Mittwoch, August 14th, 2019Microsoft Windows Server 2016 & 2019 – Windows Search is disabled by default
Samstag, August 3rd, 2019 Microsoft Windows Server 2016 & 2019 – this is because indexing of the volumes can cause problems in certain scenarios such as with Cluster Shared Volumes (CSV) and in running Remote Desktop Session Host (RDSH) with multiple simultaneous sessions
Microsoft Windows Server 2016 & 2019 – this is because indexing of the volumes can cause problems in certain scenarios such as with Cluster Shared Volumes (CSV) and in running Remote Desktop Session Host (RDSH) with multiple simultaneous sessions
c:\services.msc
Microsoft Hyper-V Server 2019 – has specific hardware requirements to run virtualization in a secure and performant way
Donnerstag, Juli 18th, 2019 Microsoft Hyper-V Server 2019 – requirements
Microsoft Hyper-V Server 2019 – requirements
Microsoft Office 365 ProPlus – will be supported on Windows Server 2019
Montag, Juli 15th, 2019Microsoft Local Administrator Password Solution (LAPS) 6.2 – provides management of local account passwords of domain joined computers
Mittwoch, Juni 26th, 2019 Microsoft Local Administrator Password Solution (LAPS) – to automatically manage local administrator passwords on domain joined computers so that passwords are unique on each managed computer, randomly generated, and securely stored in Active Directory infrastructure. The solution is built on Active Directory infrastructure and does not require other supporting technologies. LAPS uses a Group Policy client-side extension (CSE) that you install on managed computers to perform all management tasks. The solution’s management tools provide easy configuration and administration
Microsoft Local Administrator Password Solution (LAPS) – to automatically manage local administrator passwords on domain joined computers so that passwords are unique on each managed computer, randomly generated, and securely stored in Active Directory infrastructure. The solution is built on Active Directory infrastructure and does not require other supporting technologies. LAPS uses a Group Policy client-side extension (CSE) that you install on managed computers to perform all management tasks. The solution’s management tools provide easy configuration and administration
StarWind V2V Converter – ist für das Migrieren und Kopieren virtueller Maschinen zwischen Hosts mit unterschiedlichen Hypervisoren verwendbar
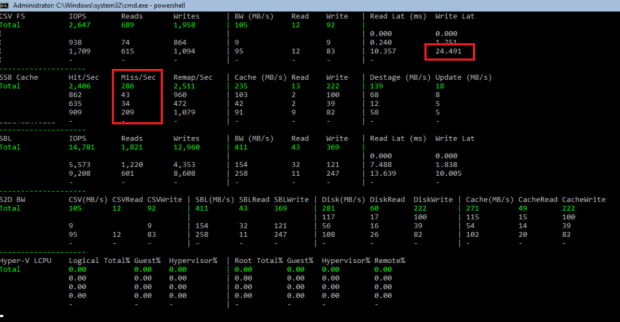
Freitag, Juni 14th, 2019Microsoft Windows Server 2019 Storage Spaces Direct (S2D) – detect a lack of cache
Montag, Juni 10th, 2019Disk Defragmentation best practice – are you looking for information on defragmentation of your vmsf datastores or defragmentation within the guest os
Sonntag, Juni 9th, 2019 The answer is NO defragmentation for both – defragmentation also generates more I/O to the disk. This could be more of a concern to customers than any possible performance improvement that might be gained from the defrag. I should point out that I have read that, internally at VMware, we have not observed any noticeable improvement in performance after a defragmentation of Guest OSes residing on SAN or NAS based datastores. I also want to highlight an additional scenario that uses an array based technology rather than a vSphere technology. If your storage array is capable of moving blocks of data between different storage tiers (SSD/SAS/SATA), e.g. EMC FAST, then defragmentation of the Guest OS doesn’t really make much sense. If your VM has been running for some time on tiered storage, then in all likelihood the array has already learnt where the hot-blocks are, and has relocated these onto the SSD. If you now go ahead and defrag, and move all of the VM’s blocks around again, the array is going to have to relearn where the hot-spots are
The answer is NO defragmentation for both – defragmentation also generates more I/O to the disk. This could be more of a concern to customers than any possible performance improvement that might be gained from the defrag. I should point out that I have read that, internally at VMware, we have not observed any noticeable improvement in performance after a defragmentation of Guest OSes residing on SAN or NAS based datastores. I also want to highlight an additional scenario that uses an array based technology rather than a vSphere technology. If your storage array is capable of moving blocks of data between different storage tiers (SSD/SAS/SATA), e.g. EMC FAST, then defragmentation of the Guest OS doesn’t really make much sense. If your VM has been running for some time on tiered storage, then in all likelihood the array has already learnt where the hot-blocks are, and has relocated these onto the SSD. If you now go ahead and defrag, and move all of the VM’s blocks around again, the array is going to have to relearn where the hot-spots are
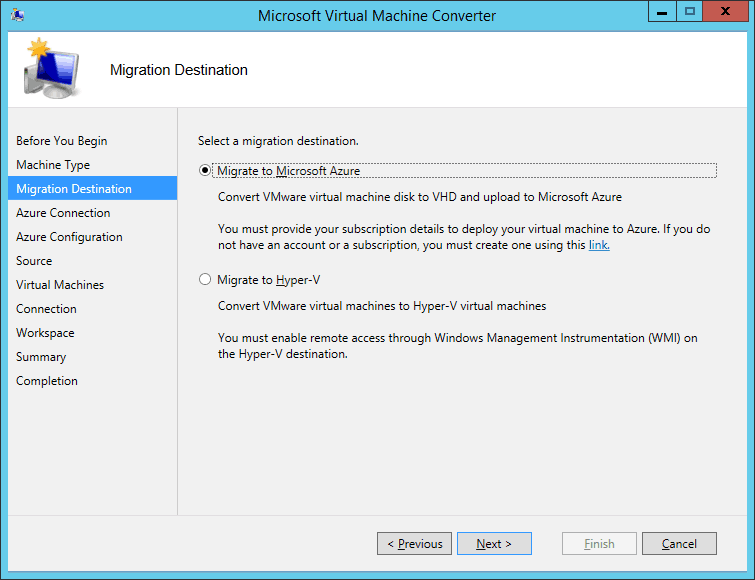
Microsoft Virtual Machine Converter (MVMC) 3.0 – to convert virtual machines and disks from VMware hosts to Hyper-V hosts and Windows Azure or convert computers and disks to Hyper-V hosts
Dienstag, Juni 4th, 2019 Microsoft Virtual Machine Converter (MVMC) 3.0 – is a freely-available tool provided by Microsoft for the purpose of converting VMware virtual machines and physical computers to Hyper-V virtual machines
Microsoft Virtual Machine Converter (MVMC) 3.0 – is a freely-available tool provided by Microsoft for the purpose of converting VMware virtual machines and physical computers to Hyper-V virtual machines