Archive for Januar, 2018
The National Security Agency (NSA) – is losing its top talent at a worrisome rate as highly skilled personnel, some disillusioned with the spy service’s leadership and an unpopular reorganization, take higher-paying, more flexible jobs in the private sector
Donnerstag, Januar 4th, 2018Raspberry Pi – join in Windows Active Directory Domain with Samba Winbindd
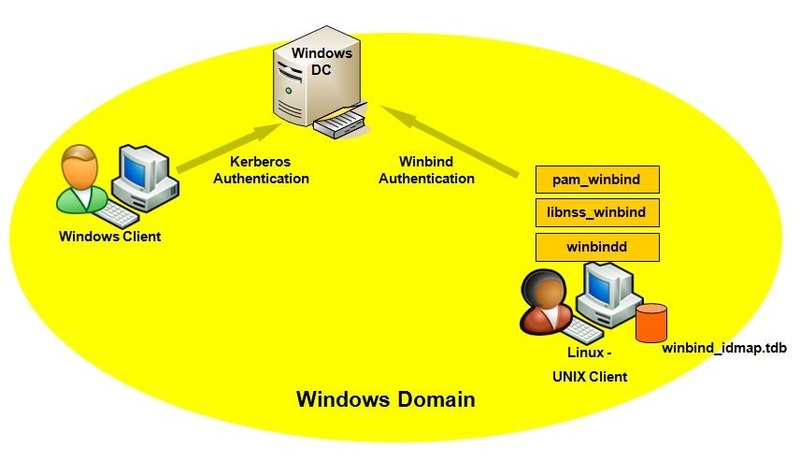
Donnerstag, Januar 4th, 2018![]() Samba’s winbindd service provides an interface for the Name Service Switch (NSS) and enables domain users to authenticate to AD when logging into the local System – using winbindd provides the benefit that you can enhance the configuration to share directories and printers without installing additional software
Samba’s winbindd service provides an interface for the Name Service Switch (NSS) and enables domain users to authenticate to AD when logging into the local System – using winbindd provides the benefit that you can enhance the configuration to share directories and printers without installing additional software
root@rpi-va-dom-1:~# apt-get update
root@rpi-va-dom-1:~# apt-get dist-upgrade -y
— verify that the /etc/hosts file on the DC correctly resolves the fully-qualified domain name (FQDN) and short host name to the LAN IP address of the DC
root@rpi-va-dom-1:~# vi /etc/hosts
192.168.1.101 VA-DC-101.VA-DOM-1.LOCAL VA-DC-101
root@rpi-va-dom-1:~# apt-get install ntp
root@rpi-va-dom-1:~# vi /etc/ntp.conf
server VA-DC-101.VA-DOM-1.LOCAL
root@rpi-va-dom-1:~# ntpq -p
remote refid st t when poll reach delay offset jitter
=========================================
VA-DC-101.VA-DO .LOCL. 1 u 231 1024 373 5.894 -259.00 641.726
0.debian.pool.n .POOL. 16 p – 64 0 0.000 0.000 0.002
1.debian.pool.n .POOL. 16 p – 64 0 0.000 0.000 0.002
2.debian.pool.n .POOL. 16 p – 64 0 0.000 0.000 0.002
3.debian.pool.n .POOL. 16 p – 64 0 0.000 0.000 0.002
+zepto.mcl.gg 192.53.103.108 2 u 689 1024 377 49.519 -9.376 7.328
+ns1.blazing.de 213.172.96.14 2 u 728 1024 377 39.998 0.032 6.335
+ntp1.rrze.uni-e .DCFp. 1 u 540 1024 377 39.858 0.574 15.616
*metasntp12.admi .MRS. 1 u 650 1024 377 39.141 0.199 4.695
+b.fu110.de 131.188.3.221 2 u 634 1024 377 34.438 -0.872 16.808
+estoma.de 85.220.190.246 3 u 621 1024 377 84.043 -17.919 15.931
+li1655-15.membe 129.70.132.32 3 u 764 1024 377 37.483 -1.305 5.944
-www.mcr42.de 195.13.1.153 3 u 651 1024 377 55.607 -6.530 6.450
+ns.km33237.keym 192.53.103.108 2 u 603 1024 377 50.298 -3.585 7.295
-213.251.53.187 195.66.241.3 2 u 976 1024 277 39.773 -2.600 9.272
root@rpi-va-dom-1:~# apt-get install samba samba-common smbclient
root@rpi-va-dom-1:~# service smbd status
root@rpi-va-dom-1:~# service nmbd status
root@rpi-va-dom-1:~# smbd -V
root@rpi-va-dom-1:~# /etc/init.d/samba stop
root@rpi-va-dom-1:~# /etc/init.d/winbind stop
— verify that no Samba processes are running
root@rpi-va-dom-1:~# ps ax | egrep „samba|smbd|nmbd|winbindd“
— remove the existing smb.conf file to list the path to the file
root@rpi-va-dom-1:~# smbd -b | grep „CONFIGFILE“
CONFIGFILE: /etc/samba/smb.conf
root@rpi-va-dom-1:~# cp /etc/samba/smb.conf /etc/samba/smb.conf.<date>
root@rpi-va-dom-1:~# rm /etc/samba/smb.conf
— remove all Samba database files, such as *.tdb and *.ldb files to list the folders containing Samba databases
root@rpi-va-dom-1:~# smbd -b | egrep „LOCKDIR|STATEDIR|CACHEDIR|PRIVATE_DIR“
LOCKDIR: /var/run/samba
STATEDIR: /var/lib/samba
CACHEDIR: /var/cache/samba
PRIVATE_DIR: /var/lib/samba/private
root@rpi-va-dom-1:~# rm –f /var/lib/samba/*.[lt]db
root@rpi-va-dom-1:~# rm –f /var/lib/samba/private/*.[lt]db
root@rpi-va-dom-1:~# apt-get install winbind libpam-winbind libnss-winbind krb5-config resolvconf
— specify realm
Configuring Kerberos Authentication – when users attempt to use Kerberos and specify a principal or user Name without specifying what administrative Kerberos realm that principal belongs to, the system appends the default realm. The default realm may also be used as the realm of a Kerberos service running on the local machine. Often, the default realm is the uppercase version of the local DNS domain
Default Kerberos version 5 realm:
VA-DOM-1.LOCAL
— specify the hostname of AD DS
Configuring Kerberos Authentication – enter the hostnames of Kerberos servers in the VA-DOM-1.LOCAL Kerberos realm separated by spaces
Kerberos servers for your realm:
VA-DC-101.VA-DOM-1.LOCAL
— specify the hostname of AD DS
Configuring Kerberos Authentication – enter the hostname of the administrative (password changing) server for the VA-DOM-1.LOCAL Kerberos realm
Administrative server for your Kerberos realm:
VA-DC-101.VA-DOM-1.LOCAL
root@rpi-va-dom-1:~# vi /etc/krb5.conf
[libdefaults]
default_realm = VA-DOM-1.LOCAL
ticket_lifetime = 24000
clock_skew = 300
dns_lookup_realm = false
dns_lookup_kdc = true
root@rpi-va-dom-1:~# vi /etc/samba/smb.conf
— line 29: change workgroup name to the one for AD DS and add lines like follows
workgroup = VA-DOM-1
# password server = VA-DC-101.VA-DOM-1.LOCAL
realm = VA-DOM-1.LOCAL
security = ads
idmap config * : range = 16777216-33554431
template homedir = /home/%U
template shell = /bin/bash
winbind use default domain = true
winbind offline logon = false
root@rpi-va-dom-1:~# vi /etc/nsswitch.conf
— line 7: add like follows
passwd: compat winbind
group: compat winbind
shadow: compat winbind
root@rpi-va-dom-1:~# vi /etc/pam.d/common-session
— add to the end if you need (auto create a home directory when initial login)
session optional pam_mkhomedir.so skel=/etc/skel umask=0077
root@rpi-va-dom-1:~# vi /etc/network/interfaces
— change name server to AD’s one
dns-nameservers 192.168.1.101
— join in Active Directory ( net ads join -U [AD’s admin user])
root@rpi-va-dom-1:~# net ads join -U Administrator
Enter Administrator’s password:
ldb: unable to stat module /usr/lib/x86_64-linux-gnu/samba/ldb : No such file or directory
Using short domain name — VA-DOM-1
Joined ‚SMB‘ to dns domain ‚VA-DOM-1.LOCAL‘
No DNS domain configured for smb. Unable to perform DNS Update.
DNS update failed: NT_STATUS_INVALID_PARAMETER
— the DNS error can be ignored make sure you create an A record and a PTR record manually
root@rpi-va-dom-1:~# systemctl restart winbind
— sending a Winbindd Ping
root@rpi-va-dom-1:~# wbinfo –ping-dc
checking the NETLOGON for domain[VA-DOM-1] dc connection to „VA-DC-101.va-dom-1.local“ succeeded
— two simple test to see if your DC is alive
root@rpi-va-dom-1:~# net ads testjoin
Join is OK
root@rpi-va-dom-1:~# wbinfo -t
checking the trust secret for domain VA-DOM-1 via RPC calls succeeded
— try to show domain users info
root@rpi-va-dom-1:~# wbinfo -u
administrator
gast
krbtgt
— try to show domain group info
root@rpi-va-dom-1:~# wbinfo -g
— try to switch to an AD user
root@rpi-va-dom-1:~# su – Administrator
Creating directory ‚/home/Administrator‘.
administrator@rpi-va-dom-1:~ $
— looking up Domain Users and Groups
root@rpi-va-dom-1:/# getent passwd VA-DOM-1\\Administrator
administrator:*:16777216:16777216::
/home/administrator:/bin/bashdom1:~ $
root@rpi-va-dom-1:~# addgroup solution
root@rpi-va-dom-1:~# adduser dp –ingroup solution
root@rpi-va-dom-1:~# mkdir -p /sharing/{JSHOgroup,JSHOpowergroup,JSHOadmingroup}
root@rpi-va-dom-1:~# chmod -R 0770 /sharing/
root@rpi-va-dom-1:~# chgrp -R solution /sharing/
root@rpi-va-dom-1:~# ulimit -n 16384
root@rpi-va-dom-1:~# vi /etc/security/limits.conf
* – nofile 1638
— configure samba shares
root@rpi-va-dom-1:~# vi /etc/samba/smb.conf
[JSHOgroup]
comment = JSHOgroup
path = /sharing/JSHOgroup/
valid users = @“VA-DOM-1\JSHOgroup“, @“VA-DOM-1\JSHOpowergroup“, @“VA-DOM-1\JSHOadmingroup“
force group = „solution“
writable = yes
read only = no
force create mode = 0660
create mask = 0777
directory mask = 0777
force directory mode = 0770
access based share enum = yes
hide unreadable = yes
[JSHOpowergroup]
comment = JSHOpowergroup
path = /sharing/JSHOpowergroup/
valid users = @“VA-DOM-1\JSHOpowergroup“, @“VA-DOM-1\JSHOadmingroup“
force group = „solution“
writable = yes
read only = no
force create mode = 0660
create mask = 0777
directory mask = 0777
force directory mode = 0770
access based share enum = yes
hide unreadable = yes
[JSHOadmingroup]
comment = JSHOadmingroup
path = /sharing/JSHOpowergroup/
valid users = @“VA-DOM-1\JSHOadmingroup“
force group = „solution“
writable = yes
read only = no
force create mode = 0660
create mask = 0777
directory mask = 0777
force directory mode = 0770
access based share enum = yes
hide unreadable = yes
root@rpi-va-dom-1:~# testparm
Load smb config files from /etc/samba/smb.conf
Processing section „[homes]“
Processing section „[JSHOgroup]“
Processing section „[JSHOpowergroup]“
Processing section „[JSHOadmingroup]“
Loaded services file OK.
WARNING: You have some share names that are longer than 12 characters.
These may not be accessible to some older clients.
(Eg. Windows9x, WindowsMe, and smbclient prior to Samba 3.0.)
Server role: ROLE_DOMAIN_MEMBER
Mercedes-Benz 2018 S-Class Sedan – Beyond The Best
Mittwoch, Januar 3rd, 2018Citrix XenMobile Service – gives IT the ability to manage a wide range of device types and applications
Mittwoch, Januar 3rd, 2018Intel Prozessoren – erste Details zur Sicherheitslücke in den CPUs
Mittwoch, Januar 3rd, 2018 Der von den Linux-Entwicklern für diesen Hardware-Bug in Intel-CPUs jetzt eingebaute Workaround namens Kernel Page-Table Isolation (KPTI) sorgt dafür dass der Speicherbereich des Kernels nicht mehr in den Speicherbereich der Prozesse gemappt wird. Mit Kernel Page-Table Isolation sieht ein Prozess also nur noch seinen eigenen Speicherbereich der Speicherbereich des Kernels ist für ihn schlicht unsichtbar sodass eine offenbar leicht auszuhebelnde Zugriffsprüfung keine Rolle mehr spielt
Der von den Linux-Entwicklern für diesen Hardware-Bug in Intel-CPUs jetzt eingebaute Workaround namens Kernel Page-Table Isolation (KPTI) sorgt dafür dass der Speicherbereich des Kernels nicht mehr in den Speicherbereich der Prozesse gemappt wird. Mit Kernel Page-Table Isolation sieht ein Prozess also nur noch seinen eigenen Speicherbereich der Speicherbereich des Kernels ist für ihn schlicht unsichtbar sodass eine offenbar leicht auszuhebelnde Zugriffsprüfung keine Rolle mehr spielt
Ob Unterstützung für Kernel Page-Table Isolation in den laufenden Kernel eingebaut ist verrät die Ausführung des Befehls „zgrep CONFIG_PAGE_TABLE_ISOLATION /proc/config.gz“ falls die Ausgabe „CONFIG_PAGE_TABLE_ISOLATION=y“ lautet dann unterstützt der laufende Kernel Page-Table Isolation (KPTI)

Schweden Trelleborgs Hamn AB – online webcam
Mittwoch, Januar 3rd, 2018Honda Adventure Roads – Nordkapp
Mittwoch, Januar 3rd, 2018Plextor M9Pe PCIe-3.0-x4 1TB NVMe SSD – up to 3,200 MB/s sequential reads and write up to 2,100 MB/s
Mittwoch, Januar 3rd, 2018Notdienst Düsseldorfer Ärzte e.V. – Ihre Arztsuche in Düsseldorf
Mittwoch, Januar 3rd, 2018Der innere Schweinehund – einmal zum Anschauen
Dienstag, Januar 2nd, 2018
Citrix ShareFile – for Healthcare
Dienstag, Januar 2nd, 2018India’s $160 billion IT industry – laid off more than 56,000 employees this year
Dienstag, Januar 2nd, 2018Horse Tail Lights – LED light strips for horses tail allowing for high visibility
Dienstag, Januar 2nd, 2018DietPi – ‚dietpi-config‘ is a feature rich configuration tool for your device
Dienstag, Januar 2nd, 2018