Dieses Update behebt ein bekanntes Problem das den Lokalen Sicherheitsautoritätssubsystemdienst (LSASS) betrifft es kann Speicherverlusten auf Domänencontrollern (DCs) dieses Problem tritt auf nachdem Sie das Update vom 12.03.2024 installiert haben das Leck tritt auf wenn lokale und cloudbasierte Active Directory DCs Kerberos Authentifizierungsanforderungen verarbeiten dieser erhebliche Verlust kann zu einer übermäßigen Speicherauslastung führen aus diesem Fall reagiert LSASS möglicherweise nicht mehr und die DCs werden neu gestartet wenn sie dies nicht erwarten
Dieses Update behebt ein bekanntes Problem das den Lokalen Sicherheitsautoritätssubsystemdienst (LSASS) betrifft es kann Speicherverlusten auf Domänencontrollern (DCs) dieses Problem tritt auf nachdem Sie das Update vom 12.03.2024 installiert haben das Leck tritt auf wenn lokale und cloudbasierte Active Directory DCs Kerberos Authentifizierungsanforderungen verarbeiten dieser erhebliche Verlust kann zu einer übermäßigen Speicherauslastung führen aus diesem Fall reagiert LSASS möglicherweise nicht mehr und die DCs werden neu gestartet wenn sie dies nicht erwarten
Archive for the ‘Windows Server 2012’ Category
Microsoft Windows Server 2022 2019 2016 2012 R2 – mit einem wichtigen Out-of-band Update und dieses behebt ein bekanntes Problem das den Lokalen Sicherheitsautoritätssubsystemdienst (LSASS) betrifft
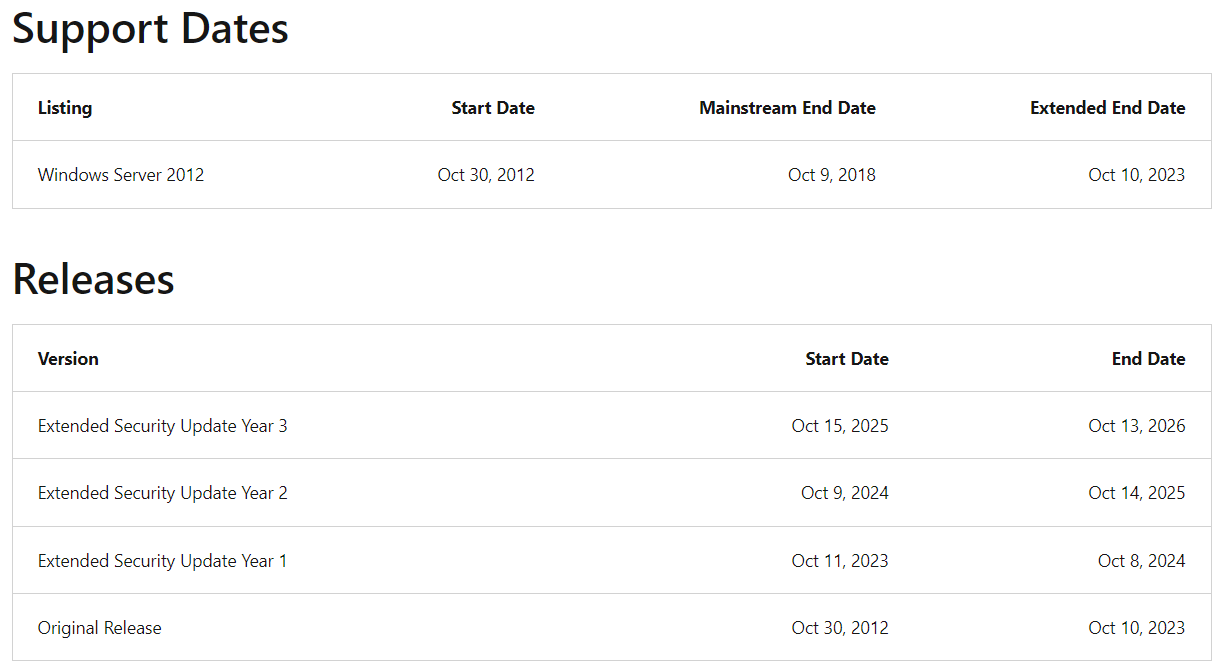
Samstag, März 23rd, 2024Microsoft Windows Server 2012 ‚Extended Security Update (ESU)‘ – gives administrators an extra three years
Montag, November 13th, 2023Microsoft Windows Server 2012 and its Windows Server 2012 R2 update – today the end of support has been reached
Dienstag, Oktober 10th, 2023
Microsoft Windows Server 2012 and its Windows Server 2012 R2 update – reaching the end of their lifecycles on October 10, 2023
Mittwoch, Oktober 4th, 2023
Microsoft Windows Server 2012 R2 – der erweiterte Microsoft Support endet am 23. Oktober 2023
Sonntag, Januar 1st, 2023
Microsoft Windows Server 2012 2016 2019 – updates released during the November Patch Tuesday that might lead to freezes and restarts on some domain controllers
Samstag, November 26th, 2022 Microsoft Workaround – until a fix is available to address this LSASS memory leak issue a temporary solution allows IT admins to work around domain controller instability
Microsoft Workaround – until a fix is available to address this LSASS memory leak issue a temporary solution allows IT admins to work around domain controller instability
Microsoft .NET Core 2.1 3.1 .NET 5.0 – updates are coming to Microsoft Update
Sonntag, September 18th, 2022 These updates will not be installed via Microsoft Update to computers with a Client operating system that have a supported major/minor version such as .NET Core 2.1, 3.1 or .NET 5.0 already installed
These updates will not be installed via Microsoft Update to computers with a Client operating system that have a supported major/minor version such as .NET Core 2.1, 3.1 or .NET 5.0 already installed
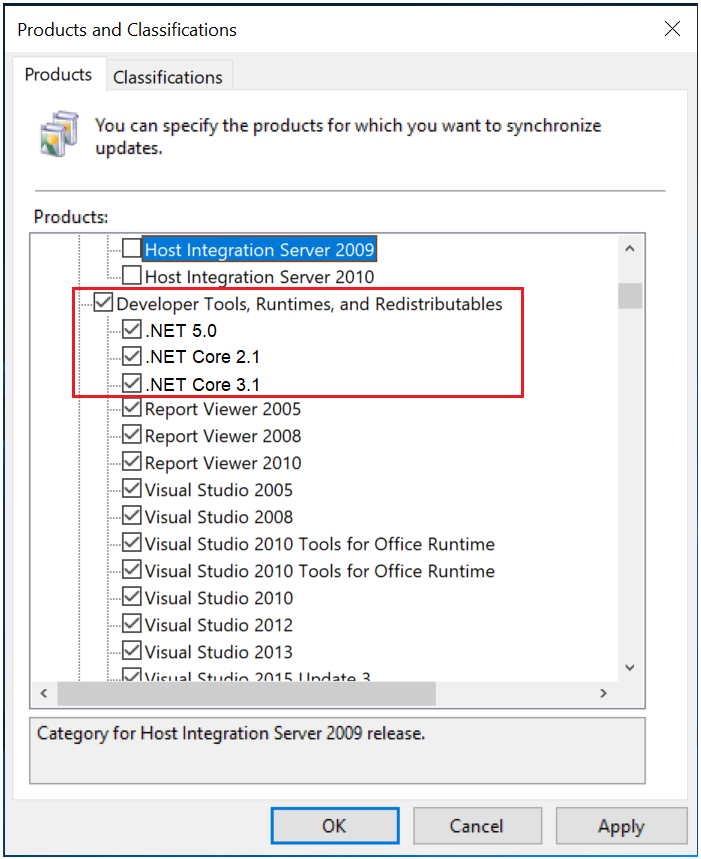
Microsoft .NET Core 2.1 3.1 .NET 5.0 – updates are coming to Microsoft Update
Donnerstag, September 15th, 2022 Configuring Products for synchronization in Windows Server Update Services (WSUS) Products – Updates for .NET Core will be published under .NET Core 2.1 .NET Core 3.1 .NET 5.0 products in WSUS and these products are nested under the Developer Tools Runtimes and Redistributables top level product
Configuring Products for synchronization in Windows Server Update Services (WSUS) Products – Updates for .NET Core will be published under .NET Core 2.1 .NET Core 3.1 .NET 5.0 products in WSUS and these products are nested under the Developer Tools Runtimes and Redistributables top level product
.NET Core Version Registry Key Name Value
Block all .NET Core updates [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NET] “BlockMU” dword:00000001
Block .NET 6.0 updates [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NET\6.0] “BlockMU” dword:00000001
Block .NET 5.0 updates [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NET\5.0] “BlockMU” dword:00000001
Block Core 3.1 updates [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NET\3.1] “BlockMU” dword:00000001
Block Core 2.1 updates [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NET\2.1] “BlockMU” dword:00000001
Microsoft Windows Server 2012 2016 2019 2022 – ausführen von STRG+ALT+DEL in einer mehrfachen Remote Desktop Session
Dienstag, März 1st, 2022 Die Bildschirmtastatur (OSK) – ist eine virtuelle Tastatur auf ihrem Bildschirm mit der sie auch ihr Passwort ändern können und so geht’s:
Die Bildschirmtastatur (OSK) – ist eine virtuelle Tastatur auf ihrem Bildschirm mit der sie auch ihr Passwort ändern können und so geht’s:
Drücken sie Windows-Taste+R um das Dialogfeld ”Ausführen” aufzurufen geben sie im Dialogfeld ”Ausführen” ‚osk‘ ein und drücken sie die Eingabetaste um die Bildschirmtastatur zu starten halten sie als nächstes die Tastenkombination STRG+ALT auf ihrer physischen Tastatur und klicken sie nun auf die ENTF-Taste mit der OSK Tastatur und minimieren sie die virtuelle Tastatur und klicken sie auf Passwort ändern
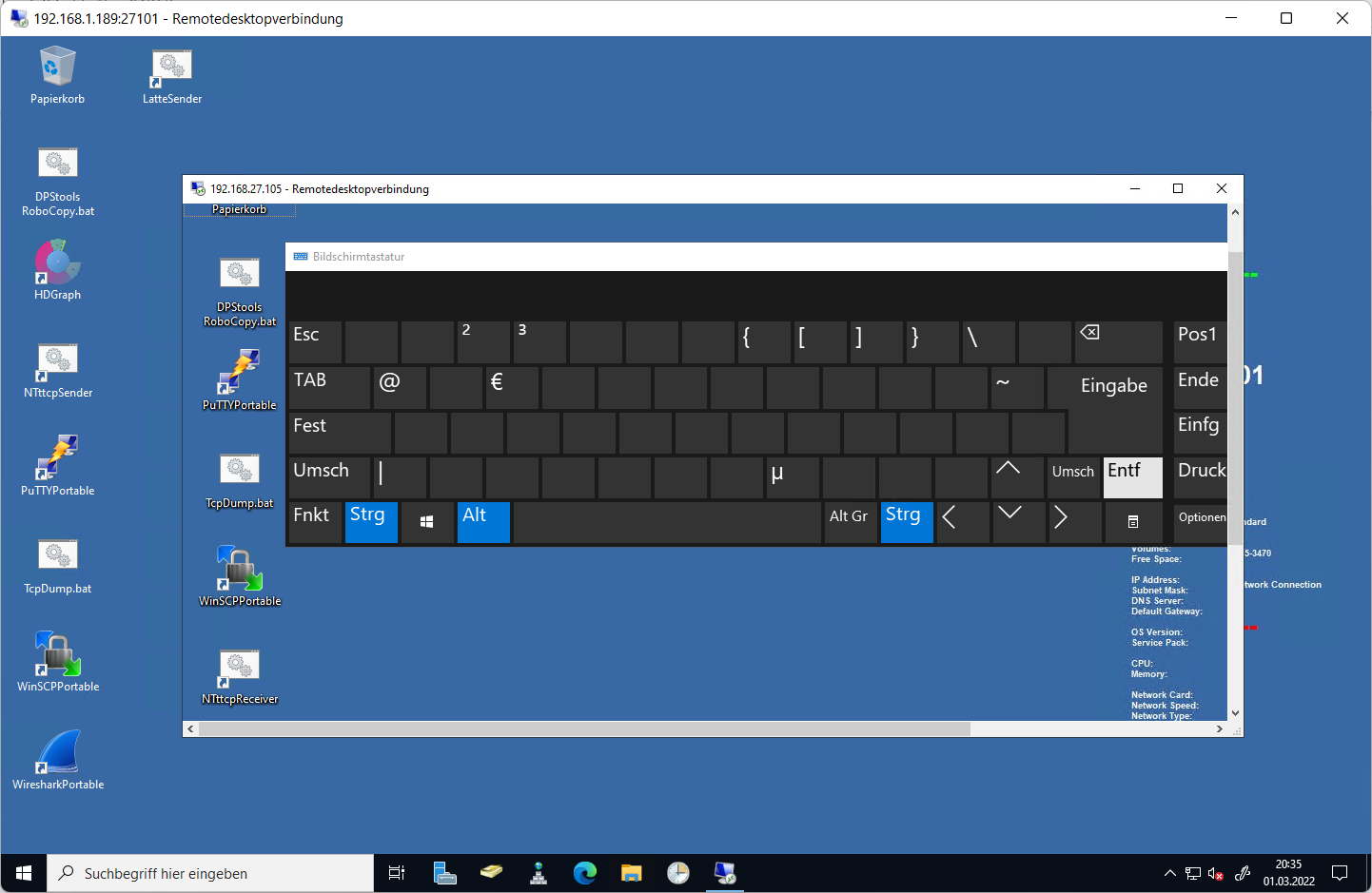
Microsoft Windows Server 2012 2016 2019 2022 – ausführen von STRG+ALT+DEL in einer Remote Desktop Session
Donnerstag, Februar 24th, 2022Verwenden Sie STRG+ALT+END anstelle von STRG+ALT+DEL

Apache Guacamole 1.4.0 – is not compatible with the default encryption of Windows if you disable NLA it should work
Mittwoch, Januar 19th, 2022 Apache Guacamole – open the registry editor ‚regedit‘ and make the following settings
Apache Guacamole – open the registry editor ‚regedit‘ and make the following settings
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp]
Change “SecurityLayer” value to dword:00000001
Verify “UserAuthentication” value is dword:0x00000000
This should work without reboot
Microsoft Windows Server 2012 – KB5010797 Out-of-Band-Update 17.01.2022
Dienstag, Januar 18th, 2022 Microsoft Windows Server 2012 – KB5010797 Out-of-Band-Update 17.01.2022
Microsoft Windows Server 2012 – KB5010797 Out-of-Band-Update 17.01.2022
Microsoft Windows Server 2012 / 2016 / 2019 / 2022 – Domain Controller Boot Loop from Windows Monthly Rollup Update January 2022
Mittwoch, Januar 12th, 2022The latest Windows Server updates are causing severe issues for administrators with domain controllers having spontaneous reboots Hyper-V not starting and inaccessible ReFS volumes until the updates are rolled back
Eine Lösung scheint die Deinstallation von KB50009624 und KB009595 auf betroffenen Systemen mittels Konsolenkommandos zu sein z.B.: für Microsoft Windows Server 2012
wusa /uninstall /kb:5009595 /quiet
wusa /uninstall /kb:5009624 /quiet
Microsoft Power BI Desktop – analyse the Windows ‚perfmon‘ log data to diagnose virtual machine performance issues
Samstag, Januar 8th, 2022(c) Microsoft Corporation. Alle Rechte vorbehalten.
C:\Users\js>relog -h
Microsoft ® Relog.exe (10.0.19041.546)
Dieses Programm erstellt durch die Beispielsratenänderung und/oder die Dateiformatkonvertierung neue
Leistungsindikatorenprotokolle aus den Daten in vorhandenen Protokollen. Unterstützt alle Leistungsprotokollformate,
wie komprimierte Protokolle für NT 4.0.
Syntax:
relog <Dateiname [Dateiname …]> [Optionen]
Parameter:
<Dateiname [Dateiname …]> Leistungsindikatorendatei für die Protokollierung.
Optionen:
-? Zeigt die kontextsensitive Hilfe an.
-a Ausgabe an vorhandene Binärdatei anhängen.
-c <path [path …]> Leistungsindikatoren, die von der Eingabedatei gefiltert werden sollen
-cf <Dateiname> Name\Pfad der Datei, in der Leistungsindikatoren aufgelistet werden, die in der neu
protokollierten Datei enthalten werden sollen. Standardmäßig werden
Leistungsindikatoren in der ursprünglichen Protokolldatei angezeigt.
-f <CSV|TSV|BIN|SQL> Ausgabedateiformat
-t <Wert> Jeden x-ten Datenpunkt in der neu protokollierten Datei miteinbeziehen.
Standardmäßig wird jeder Datenpunkt miteinbezogen.
-o Ausgabedateipfad oder SQL-Datenbank.
-b <dd.MM.yyyy HH:mm:ss> Anfangszeit für den ersten Eintrag, der in die Ausgabedatei geschrieben werden soll.
-e <dd.MM.yyyy HH:mm:ss> Endzeit für den letzten Eintrag, der in die Ausgabedatei geschrieben werden soll.
-config <Dateiname> Einstellungsdatei, die Befehlsoptionen enthält.
-q Leistungsindikatoren werden in der Ausgabedatei aufgelistet.
-y Antwort JA auf alle Fragen ohne Anforderung
Beispiele:
relog logfile.csv -c „\Processor(_Total)\% Processor Time“ -o logfile.blg
relog logfile.blg -cf counters.txt -f bin
relog logfile.blg -f csv -o logfile.csv -t 2
relog logfile.blg -q -o counters.txt
C:\Users\js>
Microsoft Windows Server 2012/2016/2019 – might experience a black screen slow sign in or general slowness
Mittwoch, Januar 5th, 2022 Microsoft listet auf der Windows Release Health Webseite Windows Server 2012 R2 Server 2016 sowie Server 2019 als betroffen auf während das Update KB5010215 die Probleme unter Windows Server 2012 R2 behebt löst KB5010196 es für Windows Server 2019
Microsoft listet auf der Windows Release Health Webseite Windows Server 2012 R2 Server 2016 sowie Server 2019 als betroffen auf während das Update KB5010215 die Probleme unter Windows Server 2012 R2 behebt löst KB5010196 es für Windows Server 2019